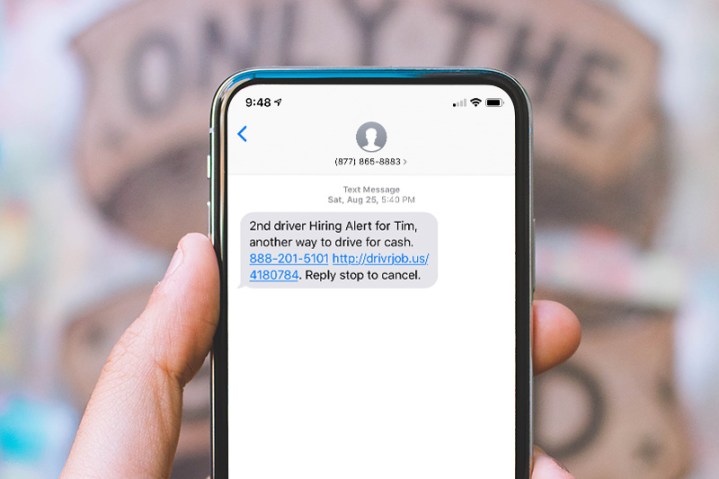
Phishing remains a serious security problem. According to some reports, one in every 101 emails are malicious and most of those use some form of phishing as a primary scamming tactic. Most people are aware of phishing, but we only look out for threats when checking email.
Criminals, however, are one step ahead. Security experts say phishing has come full-force to texting, and it carries even more potential danger than it does through email.
Breaking the myths about phones
A lot of effort goes into securing our smartphones, whether it’s passcodes, fingerprint scanners, or even facial recognition. Like the security system of a car, we assume this keeps the bad guys out and our personal data safe. But when someone falls for a phish scam over text, they are willingly handing over the keys to their car, often without knowing it.
“It’s pretty much the old phishing techniques applied to mobile text messages instead of email,” Ruby Gonzalez told Digital Trends. She’s the Communications Director at NordVPN. The company recently published a report attempting to raise awareness about how the situation has gone from bad to dire. The report calls it “smishing,” or SMS phishing.
“As smartphones get more and more popular, personal use of email is declining,” said Gonzalez. “Not only text messages, but all Facebook messages, and so on. So, people have been getting used to getting all kinds of offers being sent over messages, including links. It’s a new channel. It’s a wider channel for criminals, and they are trying to exploit it in the same way as all other channels that are opening.”
Like how masses of email accounts are collected, Gonzalez says cyber-criminals retrieve phone numbers from databases on the dark web and then try to lure their targets into sharing personal data.
The most common form of this is a text with a link that automatically downloads malware, which can then steal all sorts of different data. Your smartphone knows a lot more about you than your PC, so an installed piece of malware might steal the phone numbers in your contact list and spread the virus in hopes to exponentially multiply. Even important bits of personal data, like banking credentials or your tracking location, can be at risk.

Another tactic is to pose as a legitimate and well-known institution, a classic page out of the phishing playbook. In some cases, scammers masquerade as tax authorities, which has become an increasingly worrisome problem in the UK and Canada. During tax season, Gonzalez noted, these sorts of attacks become extremely common. The fact a message comes over text often gives a false sense of legitimacy, as many people don’t know a text message can be a threat.
“They say that the user is due a tax refund or needs to provide some more information,” said Gonzalez. “Basically, they try to get users’ financial information, and that can then be used for stealing their money.”
Whether it’s from your dentist or your library, automated text messages are more common than ever. The more accustomed we are to automated texts, the more opportunity there is for scammers to exploit that familiarity.
The more accustomed we are to automated texts, the more opportunity there is for scammers to exploit that familiarity.
A simple reply to a text message is often all that’s needed to put you in harm’s way. In the US, Gonzalez mentioned shortcodes as a commonly-exploited tactic. These are typically used by organizations like charities, which can send texts directly to supporters and allow them to donate funds with just a one-word response. Scammers have used that same system to steal money right out of people’s bank accounts.
The problem is far more widespread than you might think. According to Gonzalez, more than one and three people in the UK who text have been targeted by a phishing scam in the past six months. Statistics also say fewer than two in five people report a scam when it happens, meaning the real numbers could be even worse.
What can we do about it?
The biggest problem with phishing is that it’s hard to detect. While most people think they’d never fall victim to it, many people do, and don’t realize what’s happened until it’s far too late. As stated above, scammers prey on people’s fears about security or finances. However, there are some practical things you can do to stay one step ahead of scammers.
Related reading
- People are reading your email
- Why the password is dying
- Spam is back and worse than ever
- One in five gamers falls victim to fraud
The first is simple. Never click on a link or reply to a text. If you are even slightly suspicious, it’s always better to play it safe. That includes if the call to action is “reply if you want to stop getting these messages.” Try Googling the content of the message if it seems even slightly off.
“Sometimes criminals have huge databases of phone numbers, and if they get a reply, they know the number is active,” said Gonzalez. “So that can actually be counterproductive. If it looks like it comes from a company and it asks for strange things like a password or has a link, find the legitimate number on the internet and call and verify if the message really came from them. Not clicking on any links is a good idea, unless you’re pretty sure it’s coming from a legitimate source.”
Having anti-malware installed on your phone isn’t a bad idea, either. Some people believe that smartphones are less susceptible to malicious software than computers, but Gonzalez is convinced that the opposite was true.
“Having antimalware software for the phone is getting as important as having one on your laptop or desktop computer.”
“There are lots of malware strands that are primarily target phones,” she noted. “Specifically, Android phones, because
Several VPN companies provide additional support in this area,as well. NordVPN has its own feature in its security apps called CyberSec, which the company says is like a content blocker for your entire operating system. It works by checking addresses against the huge database of the company’s blocklists.
Lastly, if you do find yourself in a situation where you think some malware has been downloaded, make sure to protect your data. Change all your passwords, or use an encrypted password manager for maximum security.



