- Home
About
The latest Facebook news and guides, all in one place. Navigating one of the largest social media networks and keeping up with everything Mark Zuckerberg up to is no easy task, but Digital Trends offers in-depth coverage to help keep you informed. Here’s everything you need to know about Facebook.

Meta has a bold new strategy for VR
Meta just announced Horizon OS, a mixed reality operating system that Lenovo, and Asus will use in new VR headsets.



The gloves are off as The Zuck lays into Apple’s Vision Pro
Surprise, surprise ... After trying Apple's new Vision Pro, Meta boss Mark Zuckerberg says he thinks his company's Quest 3 'is the better product, period.'

The 5 best websites like Craigslist in 2024
A wide variety of alternatives to Craigslist are available -- some even have modern, easier-to-use interfaces. Check out our favorite websites like Craigslist.
How to set your Facebook Feed to show most recent posts
Facebook's Feed button allows you to see a list of chronologically sorted posts. Here's where to find and use it.
How to create multiple profiles on a Facebook account
Facebook now lets you create multiple profiles for one Facebook account. Here's how to create a new profile.

X rival Threads could be about to get millions of more users
Threads – Meta’s rival to X, formerly Twitter – is hoping to get a big boost after launching in the EU, a market with nearly half a billion people.

Asgard’s Wrath 2 is a grand finale and new beginning for VR gaming
With the impressive Asgard's Wrath 2, Meta proves that VR games can be just as enormous and content rich as anything else.
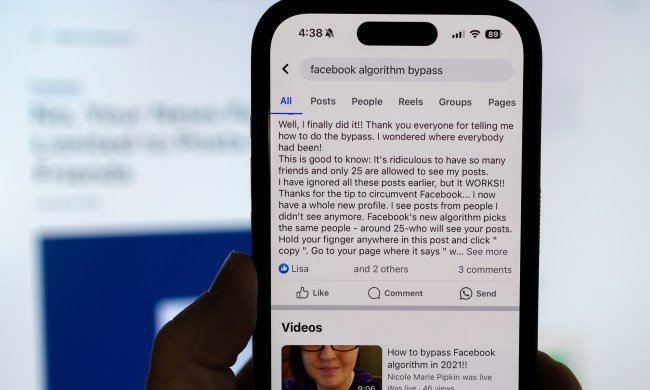
Is the Facebook algorithm bypass a scam? Or is it a hack?
No, you can't bypass the Facebook algorithm by copying and pasting a post. Not then, not now. It's just not how things work.
How to delete or deactivate your Facebook account
Whether you want to be free of Facebook forever or just need a break from it, we've got you covered. Here's how to delete or deactivate your Facebook account.

WhatsApp used to be one of my favorite apps. Now, I can’t stand it
After starting out as a hub of meaningful conversations, WhatsApp has now devolved into a digital billboard filled with spam messages and unnecessary features.

How to find your Threads ticket to show when you joined
The Threads social network has somewhere around 100 million users, and many of them are posting screenshots of the ticket that shows when they joined up.

Meta Quest 3 is here, but is the Quest 2 still worth buying?
Meta's Quest 3 has arrived with improved performance and mixed reality, but the Quest 2 costs less and has the same games, so which is right for you?

How to preorder the Meta Quest 3
Meta's Quest 3 is arriving soon. Here's how to secure your Meta Quest 3 preorder to make sure you can use the headset on release day.

Meta Quest 3 review: the VR headset you’ve been waiting for
Meta's Quest 3 costs $200 more than the Quest 2. How much have performance, graphics, mixed-reality, and comfort improved and is it worth the price?

Meta pays big bucks to end office lease that still had 18 years left
The move is a sign of the times, with tech giants and other large companies responding to the popularity of remote working since the pandemic.

Meta’s AI smart glasses collection can live stream video — but they’re missing a big feature
Ray-Ban Meta smart glasses feature 12MP cameras that can live stream directly to Instagram and Facebook, and respond to voice commands.

Facebook’s rebrand isn’t quite as drastic as Twitter’s
Facebook owner Meta has unveiled a new logo and some other design changes for the social network, though the new look is much like the old one.

Meta is reportedly working on a GPT-4 rival, and it could have dire consequences
AI and Facebook are two of today’s most scandal-prone topics, but they’re reportedly combining to make what could be the most powerful AI in the world.

How to use Meta Threads on the web
Meta's newest social media platform, Threads, is now available on the web. Here's how to access it, what to expect, and how to use it.

Zoom adds ChatGPT to help you catch up on missed calls
Video-calling app Zoom has added a new AI tool based on ChatGPT that could make virtual meetings much easier to manage. But does it respect your privacy?
Some Android phones are about to get superpowerful AI apps
MediaTek's upcoming flagship chip will offer hardware tricks that will dramatically improve generative AI apps on smartphones by using on-device processing.

Meta is building a space-age ‘universal language translator’
Meta has just announced it is building an AI translation tool that can convert over 100 languages in a variety of different ways. Will it beat the competition?

Why I gave up selling tech on Facebook Marketplace
A nightmarish week of trying to sell a MacBook and a gaming PC convinced me that Facebook Marketplace isn't worth your time for tech.