(in)Secure is a weekly column that dives into the rapidly escalating topic of cybersecurity.
Like home security, people would often rather not think about cybersecurity once they’ve paid for it. They’d rather pay and pray.
But how do you know when a security company’s software is working? With all the billions of dollars poured into protecting ourselves and our businesses online, why do hacks seem to be increasing in regularity and damages?
We spoke with Oren J. Falkowitz, a former senior-level employee at the NSA and United States Cyber Command, who has a radical idea for how cybersecurity companies should be making their money.
The problem
Our modern cybersecurity fiasco has many causes. Maybe it’s a lack of government funding and regulation. Maybe it’s large tech corporations not caring enough about privacy. Maybe it’s just a matter of educating the public and explaining in simple terms what’s at stake.
“Companies spend about $93 billion on cybersecurity, with no end in sight …”
Falkowitz has a different take. He believes the real problem is that cybersecurity profits aren’t tied to performance. “For us, it means performance-based cybersecurity and paying for results, not a failure,” he told Digital Trends. “Companies should pay for cybersecurity only when and if it performs as designed.”
That’s not how it works today. Cybersecurity experts, companies, and antivirus software are presented and purchased like an insurance plan. You pay monthly and hope that nothing bad happens. If it does, they’ll help you pick up the pieces — and maybe try to upsell you on more security.
Area 1 Security, Falkowitz’ own cybersecurity company, takes the opposite approach. Area 1 calls out the fact that people “commit to security contracts running three to five years, spending six or seven figures. But they still don’t get what they pay for.” Falkowitz believes clients should pay only for attempted crimes that are stopped. It’s an idea similar to bug bounty programs, which encourage hackers to find – and then disclose – vulnerabilities.
“Companies spend about $93 billion on cybersecurity, with no end in sight, and what’s worse, no end to the severity or frequency of cyber attacks,” Falkowitz said. “Performance-based and accountable cybersecurity will ensure that results are what drive the future innovations and successful outcomes in business models.”
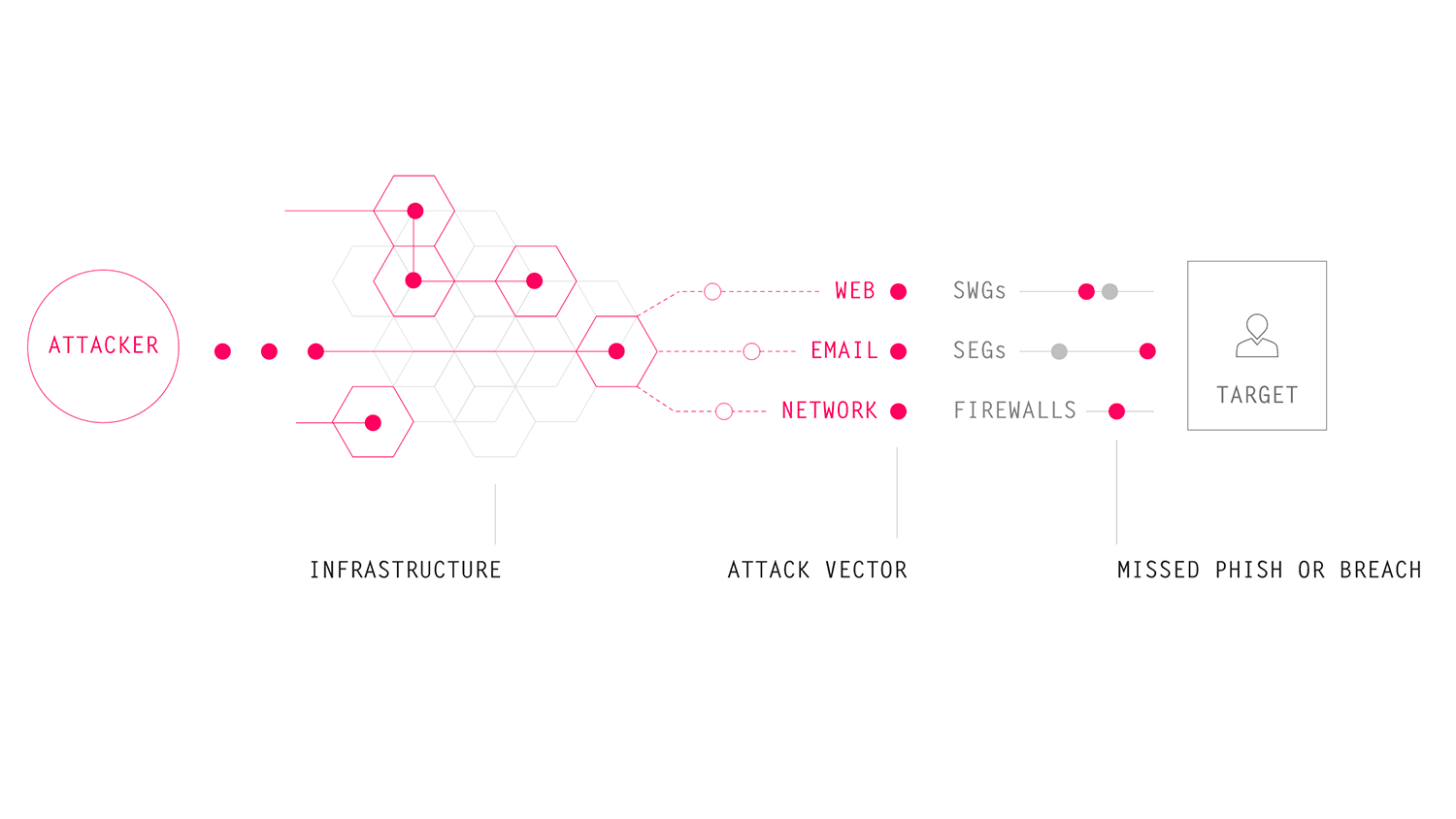
You might wonder how a company could stay in business if it constantly had to prove to customers that attacks are being stopped. Area 1 Security makes it work by focusing its efforts on a particular aspect of cybersecurity — phishing.
It all leads back to phishing
“Phishing is the attack that starts the attack, it’s the root cause for an astounding 95 percent of all damages,” said Falkowitz. “The key to performance-based cybersecurity is stopping phishing.”
“Phishing is a socially-engineered attack that relies on authenticity to evade detection.”
Phishing has become the bane of the internet’s existence. From malware to stolen data, phishing is often the entry point for the worst cyberattacks we’ve seen. It usually takes the form of a fraudulent email, sent to an unsuspecting victim under the guise of an official company or organization.
The email will then prompt the reader to click a link — and once they do, the attacker’s trap is triggered. Though simple, hackers have used phishing for everything from the Clinton campaign email debacle to the devastating 2017 WannaCry ransomware attack.
“Phishing is a socially-engineered attack that relies on authenticity to evade detection,” Falkowitz explained. “It’s designed not to be caught by anyone! That’s why it works so well. Besides being effective, it’s also incredibly cheap. That’s part of why it’s so good economically to be a bad guy on the internet. If you’re an attacker and you have something that works, that most companies can’t defend against, why not keep using it?”
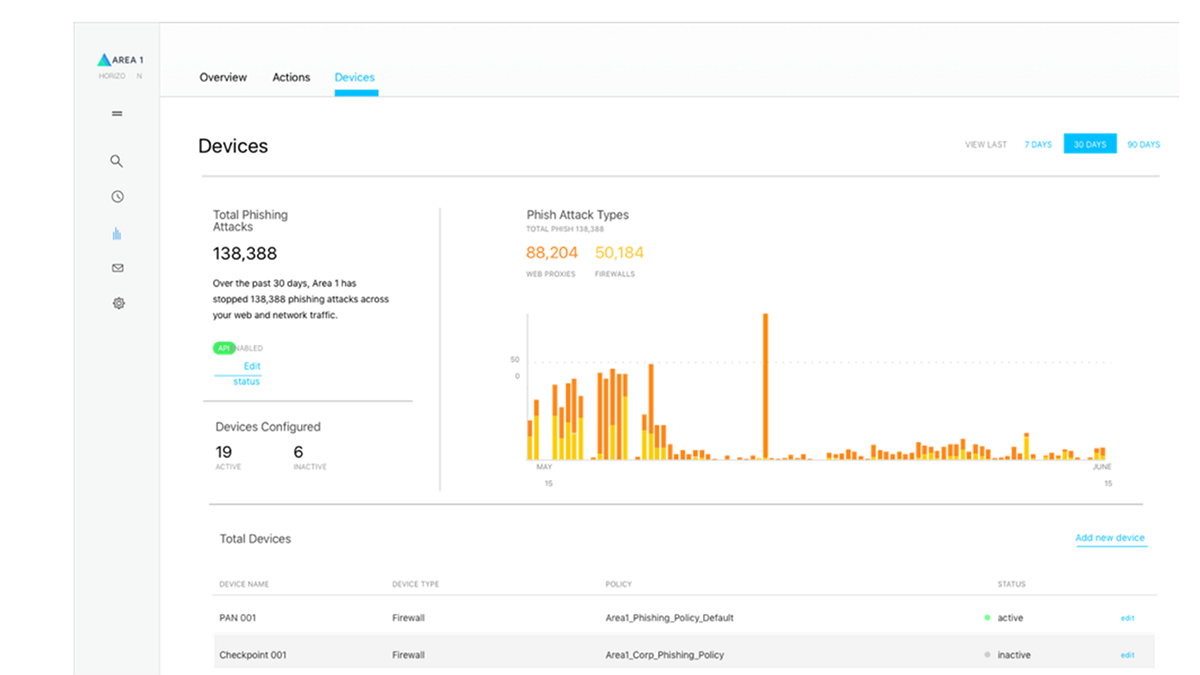
Area 1 Security’s system claims to stop 99.99 percent of all phishing attacks, allowing them to keep a log of the attacks they’re preventing. Its philosophy isn’t to hunt down the criminals across the internet, but instead to stop the ones who are already knocking at our doors.
“Until we take phishing as a weapon out of the hands of attackers, we’ll continue on this increasingly dangerous and expensive trajectory.”
Maybe it’s time we started asking more from the companies that claim to protect us. After all, disarming the bad guys sounds like a much better plan than waiting for them to attack.