Google has been running its Safe Browsing service for about four years, with a goal towards providing an open service that Web browsing applications can check against to see if a particular site is suspected of hosting malware or phishing scams. Now, Google has published an analysis (PDF) of more than 160 million Web pages on more than 8 million sites to look for trends in how malware is distributed—and finds that while social engineering tricks play a small role and plug-in and browser exploits are still common, malware distributors are increasingly turning to IP spoofing in hopes of avoiding detection.
Overall, Google finds that malware distributors rely on exploiting a vulnerability in a browser or a plug-in to install malware on users’ systems in what are known as drive-by attacks: typically, all users need to do is load a Web with the malicious code, and their systems are compromised. Google’s Safe Browsing initiative has automated tools that scan sites looking for these attempted exploits, and adds them to its database of questionable and dangerous sites if they’re found.
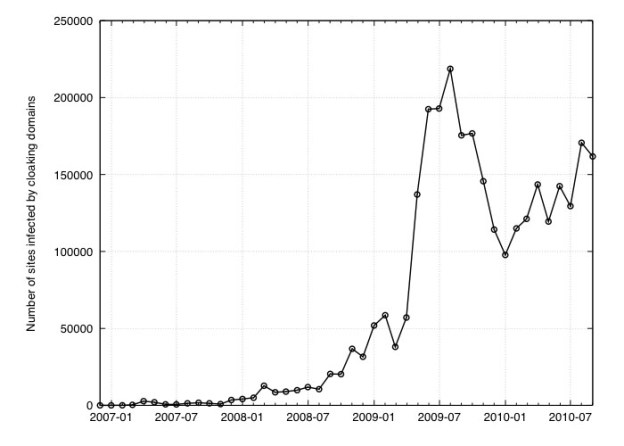
However, malware authors are increasingly turning to IP spoofing to avoid detection. In this case, the technique doesn’t involve using router trickery in order to make traffic from one source look like it comes from another; instead, the malware distributors try to detect connections from Google’s Safe Browsing survey (and services like it) and serve perfectly safe, innocuous Web pages to those services…saving its nasty payload for visitors they believe to be real users.
“The concept behind cloaking is simple: serve benign content to detection systems, but serve malicious content to normal Web page visitors,” wrote Lucas Ballard and Niels Provos in the Google Online Security blog. “Over the years, we have seen more malicious sites engaging in IP cloaking.”
Google emphasizes it is constantly adjusting its scanners with “state-of-the-art malware detection” to compensate for IP cloaking techniques, but notes malware distributors and security services will always be in an arms race…with security folks most often trying to play catch-up.
Google also notes that, with only a couple exceptions, browser and plug-in vulnerabilities used by malware distributors are only used for a comparatively short period of time: as soon as a new vulnerability is discovered—or an old one is patched—malware authors quickly move on to another exploit.
Google also notes that while getting people to install malware using social engineering—tricking people into downloading dangerous software, usually by promising a plug-in or antivirus package—is still common and on the rise, it’s employed by only about two percent of sites that distribute malware.
Editors' Recommendations
- How to remove an account from Google Smart Lock
- Hackers are using this incredibly sneaky trick to hide malware
- Chrome is making a key change to protect you from phishing
- This Google Chrome feature may save you from malware
- Chrome has a security problem — here’s how Google is fixing it


