Microsoft has detailed its latest effort to protect against various types of fraud that can happen via a method as simple as spelling a website URL incorrectly.
The company has announced as of Monday that it is adding website typo protection to its Microsoft Defender SmartScreen service, to aid against web threats such as “typosquatters.” These types of cybercrime can include phishing, malware, and other scams.
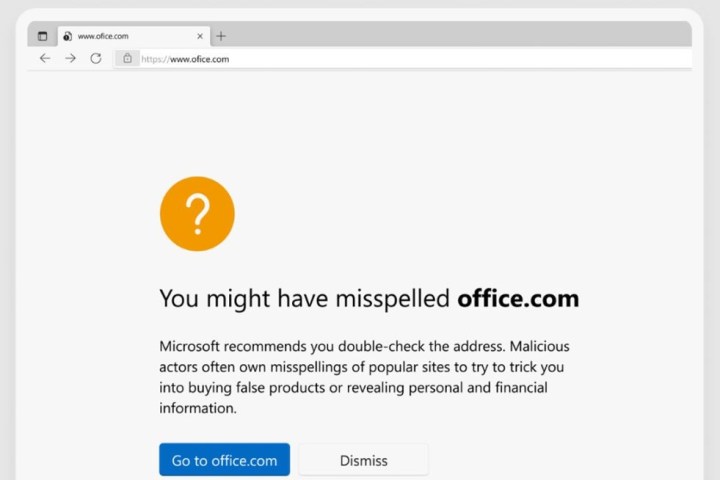
If you happen to have a typo in the website name you’re trying to input, it can send you to an alternate page that hosts “advertising sites, affiliate links, false products, fake search engine results, or in some cases by redirecting users into parked domains reserved for very short-lived phishing campaigns,” Microsoft noted.
The new Website typo protection on the Microsoft Defender SmartScreen service combats these typosquatter tactics by alerting you via a warning page when you have misspelled a URL and been directed to a typosquatting site. You will be asked to verify the site address you want to visit before you can continue, the brand added.
Microsoft has already partnered with the Bing Indexing team in order to identify new typosquatters and their webpages as soon as they pop up to keep the Microsoft Edge browser dynamically updated.
Microsoft is not always known for its preventative measures when it comes to cybersecurity. More commonly, the brand responds in the aftermath of a major exploit.
A recent zero-day vulnerability, CVE-2022-41040, and CVE-2022-41082, that was discovered in Microsoft’s Exchange email servers in early October was not only already exposed to bad actors, but it was also mistaken for a different exploit before it could be identified.
At the time, Microsoft stated it was “working on an accelerated timeline” to address the zero-day vulnerability and create a patch. However, with the exploitation already in the wild, there are ample opportunities for businesses and government entities to be attacked by bad actors. So far, there haven’t been any known attacks using the CVE-2022-41040 or CVE-2022-41082 vulnerabilities.
Editors' Recommendations
- This secret Microsoft Edge feature changed the way I work
- You can finally purge your PC of default Windows apps
- Microsoft Bing and Edge are getting a big DALL-E 3 upgrade
- AI can now steal your passwords with almost 100% accuracy — here’s how
- This PowerPoint ploy could help hackers empty your bank account




