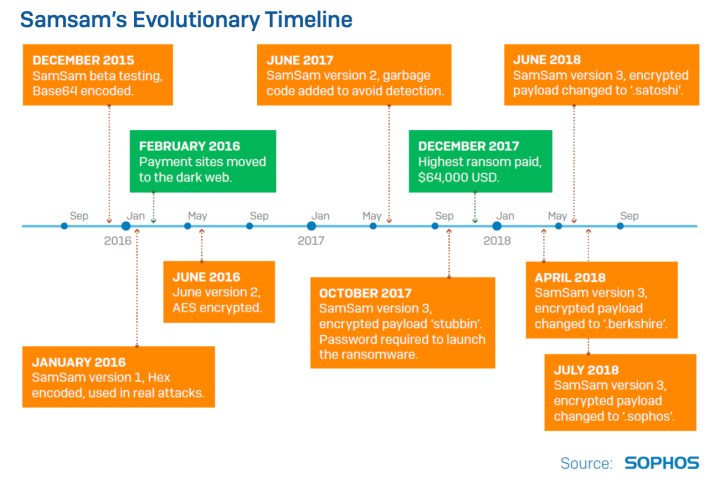
Security firm Sophos reports that the SamSam ransomware has done more financial damage than previously believed, generating $5.9 million from victims since it originally appeared in December 2015. Sophos says hackers use SamSam in attacks about once per day, but the typical web surfer will likely never experience the devastation given SamSam’s target audience.
The sole task of ransomware is to hold a PC hostage by encrypting its data. For a fee, hackers will release that data. Ransomware is typically used in untargeted email spam campaigns where recipients click on an attachment or link that installs the ransomware on their PC. These campaigns typically don’t target specific people but flood the inboxes of hundreds of thousands of individuals.
According to Sophos, SamSam is different. It’s not used in a widespread spam campaign looking to hook potential victims. Instead, a single hacker or a team of individuals breaks into a network, scans the network, and then manually runs the ransomware. They are tailored attacks to maximize the damage and generate high-dollar ransoms.
“Perhaps most eye-catching though is new information about how it spreads,” the security firm reports. “Unlike WannaCry, which exploited a software vulnerability to copy itself to new machines, SamSam is actually deployed to computers on the victim’s network in the same way, and with the same tools, as legitimate software applications.”
Originally SamSam was believed to be used to solely attack healthcare, government, and educational organizations. But a deeper investigation reveals that companies in the private sector have actually taken the brunt of the attacks but are just unwilling to come forward to reveal their forced payments.
That said, businesses in the private sector account for 50 percent of the known attacks followed by healthcare (26 percent), government (13 percent), and education (11 percent) institutions.
A chart provided with the report shows that 74 percent of the victim organizations identified by Sophos reside within the United States. The United Kingdom trails with eight percent followed by Belgium, Canada, and Australia, while other countries such as Denmark, Estonia, the Netherlands, and India are one percent. There are other victims and countries Sophos has yet to identify.
The entire ransomware problem appears to stem from weak passwords. Hackers gain access to networks through the Remote Access Protocol that typically allows executives and workers to access the network remotely from a PC while at home or during a business trip. Hackers use software to guess these weak passwords and infiltrate the network.
But unlike WannaCry and NotPetya, hackers don’t unleash a worm that crawls through the network and infects every PC. Instead, they continually pound the network’s defenses until they get around the roadblocks and retrieve the access they want — or are booted from the network. From there, they move from PC to PC.
If the attack is successful, hackers wait to see if victims make payment through a website posted on the dark web. The ransoms have increased over time, Sophos claims, to around $50,000. Untargeted ransomware attacks such as spam campaigns typically only generate three-figure ransoms.


