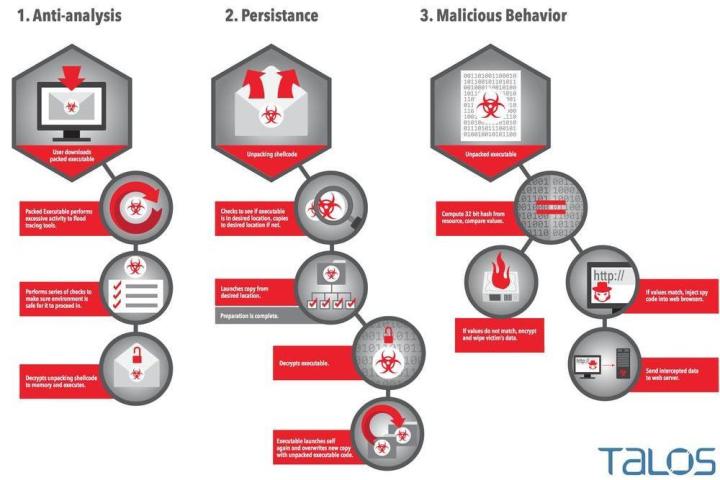
At face value, Rombertik isn’t much different from most malware distributions, acting as a keylogger for your Web browser that hunts down any information might look remotely like a username/password combination or credit card number. These types of infections are a dime a dozen these days, but what makes Rombertik newsworthy is the way in which it attempts to avoid detection if it’s picked up by an antivirus scan or found in a folder by the user themselves.
Malware with prebuilt instructions on how to avoid detection is nothing new, and any malicious program worth its salt will generally have at least one or two shields set up to keep itself away from the gaze of watchful eyes. This can be anything from hijacking the AV program itself to display false results, to deleting the infected file before a user has a chance to run it past diagnostics.
Rombertik takes these tactics to a whole different level. It will automatically format a person’s hard drive if any part of the infection senses a disturbance to its operations is about to happen. There are a number of other camouflage techniques it will use before the nuclear option, such as loading up sandbox analysis tools with 950 million lines of code at once or attempting to overwrite the master boot record (MBR) to make the computer inoperable, but if all of these fail to prevent someone from getting a look at the innards of Rombertik, it wipes the hard drive it’s been installed on and takes all your data down with it.
Realistically, the only way you might be able to coax Rombertik into self-destruct mode is if you’re a high-level researcher who knows how to get past all its other defenses first, but the fact that the threat is still there is enough to have us checking links in our email twice before making any risky clicks too quick.
Editors' Recommendations
- Bing Chat’s ads are sending users to dangerous malware sites
- This dangerous new Mac malware steals your credit card info
- In the age of ChatGPT, Macs are under malware assault
- This Mac malware can steal your credit card data in seconds
- This critical macOS flaw may leave your Mac defenseless


