Some technology flaws don’t go away—they just get a Band-Aid applied to them that eventually falls off. Adobe says it is working on a fix to an Adobe Flash vulnerability that enables attackers to trick Flash users into turning on their microphone and/or webcams, potentially enabling attackers to visually spy on them, overhear and record conversations, and obtain sensitive information. However, unlike most zero-day Flash exploits, this one doesn’t involve the Flash plug-in itself: instead, it uses interface obfuscation techniques to get users to unwittingly change their Flash player settings using a Shockwave Flash file hosted by Adobe itself.
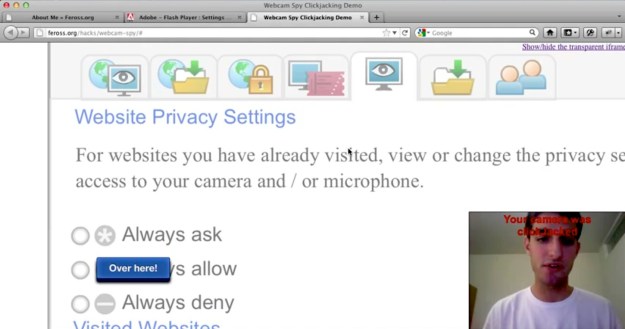
Re-discovered by Stanford computer science student Feross Aboukhadijeh, the attack works by loading Adobe’s own Flash Player Settings Manager directly from Adobe, then using CSS, JavaScript, or other techniques to hide most of the interface and encourage users to click in locations that will enable Flash access to a user’s webcam or microphone. The attack relies on trickery and social engineering to get users to click in the right locations, rather than exploiting a bug in the plug-in or the Flash Player Settings Manager.
The technique is similar to a webcam settings attack that surfaced back in 2008; however, in that case attackers were loading the Flash Player Settings file into an iframe (essentially, a sub-region of a Web page that can be treated like a separate page), and using trickery to get users to click the settings options there. Adobe changed their settings file so it couldn’t be loaded in an iframe, but Aboukhadijeh realized that wasn’t actually necessary: just load the settings manager directly from Adobe, and you bypass Adobe’s anti-framing JavaScript code.
Aboukhadijeh reported the problem to Adobe, and apparently received no response. However, after disclosing the problem publicly Adobe has contacted Aboukhadijeh and said they are working on a fix that will not require an update to the Flash Player. As a result, Adobe likely won’t issue a security bulletin about the vulnerability. According to CNet, Adobe says a fix could be deployed by the end of the week.
Adobe has long been criticized for using a Shockwave Flash file on its own servers to enable user control of users’ settings on their local machines. Computer security experts and privacy advocates have also noted it makes the process of monitoring and clearing “Flash cookies”—also known as Local Shared Objects—considerably more complicated than it needs to be.
Editors' Recommendations
- How to tell if your webcam has been hacked
- Logitech’s new webcams are an alternative to Apple Desk View
- OBSBOT Tiny 4K is a petite UHD webcam with AI-powered tracking
- The best lighting for webcam streaming 2022
- Using Zoom on a Mac? It may be secretly recording your audio


