Hackers are getting so sophisticated with malware that they are making links look like a notice about company vacation time.
A new phishing scam called “DarkGate Loader” has been uncovered that targets Microsoft Teams. It can be identified with a message and a link that reads “changes to the vacation schedule.” Clicking this link and accessing the corresponding .ZIP files can leave you vulnerable to the malware that is attached.
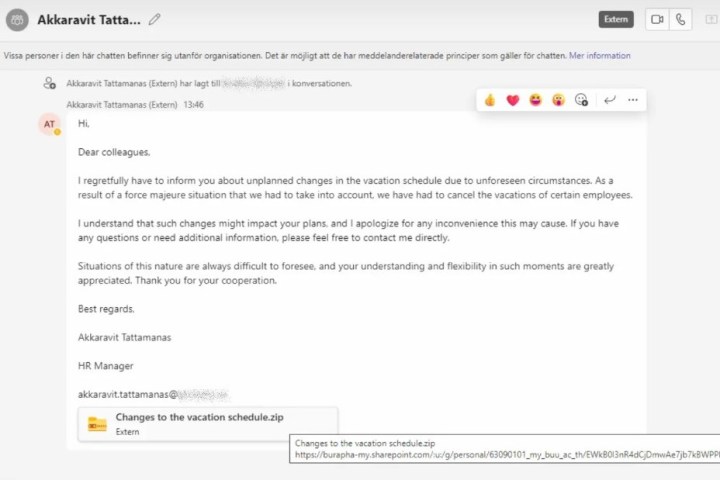
The research team Truesec has been observing DarkGate Loader since late August and notes that hackers have utilized an intricate downloading process that makes it so the file is difficult to identify as nefarious.
Hackers were able to use compromised Office 365 accounts to send the malware-infected message with the “changes to the vacation schedule” link through Microsoft Teams. Truesec found the accounts that were taken over by the hackers to send the DarkGate Loader malware. These include “Akkaravit Tattamanas” (63090101@my.buu.ac.th) and “ABNER DAVID RIVERA ROJAS” (adriverar@unadvirtual.edu.co).
The malware comprises an infected VBScript hidden within an LNK (a Windows shortcut). The research team notes that the attack is crafty due to its SharePoint URL, which makes it hard for users to realize it’s a challenged file. The precompiled Windows cURL script type also makes the code harder to identify because the code is hidden in the middle of the file.
The script is able to pinpoint if the user has the antivirus Sophos installed. If not, the malware can inject additional code, in an attack called “stacked strings,” which opens a shellcode that creates a DarkGate executable that loads into the system memory, the team added.
DarkGate Loader isn’t the only phishing scam that has been plaguing Microsoft Teams this summer. A group of Russian hackers called Midnight Blizzard were able to use a social engineering exploit to attack approximately 40 organizations in August. The hackers used Microsoft 365 accounts owned by small businesses that had already been challenged and pretended to be technical support in order to execute attacks. Microsoft has since addressed the issue, according to Windows Central.
Last fall, one common trend was business email compromise (BEC) campaigns, which are phishing scams where a nefarious actor, disguised as a company boss, sends an email that looks like a forwarded email chain, with instructions to an employee to send money.
Another infamous exploit was the Windows zero-day vulnerability Follina. Researchers discovered it in the spring of last year and determined it allowed hackers access to the Microsoft Support Diagnostic Tool that is commonly associated with Microsoft Office and Microsoft Word.
Editors' Recommendations
- The most common Microsoft Teams problems and how to fix them
- Double-check that job posting — hackers are spreading malware through them
- Hackers are using AI to create vicious malware, says FBI
- Chinese hackers targeting critical U.S. infrastructure, Microsoft warns
- You can now try out avatars and virtual spaces in Microsoft Teams




