
“Laura, at this stage I can offer nothing more than my word. I am a senior government employee in the intelligence community. I hope you understand that contacting you is extremely high risk. From now on, know that every border you cross, every purchase you make, every call you dial, every cell phone tower you pass, friend you keep, site you visit [and] subject line you type is in the hands of a system whose reach is unlimited, but whose safeguards are not.”
From this first correspondence to the very last leak, everything we knew about the Internet was going to change forever. The programs he alludes to would eventually make it onto the front page of newspapers across the country, meticulously detailing a monolithic surveillance and digital intelligence operation unlike anything the world had seen before.
Since then, the public’s desire for safe, secure, and encrypted ways to communicate has skyrocketed. It became a top trending search on Google in a matter of just a few months and has remained popular since.
SilentPhone for Desktop
When Mike Janke first announced the formation of his privacy-centric partnership SilentCircle back in 2011, he spoke about his vision of a world where digital communication over the open internet was free, protected, and immune to any outside entities who might try to steal the secrets shared by people on either side of the line.
The need for alternative solutions is greater than it’s ever been, following a leak which confirmed that the NSA and GCHQ had been actively tapping into Skype conversations to record the video of subjects they found attractive, and freely passing those captures around the office.
Silent Phone seeks to put a stop to that practice in perhaps the most obvious way possible; full and unflinching transparency, right from the very start. While the core structure of their encryption methods is closely guarded, nearly everything else in the treasure chest is open for the rest of the world to scrutinize as they will.
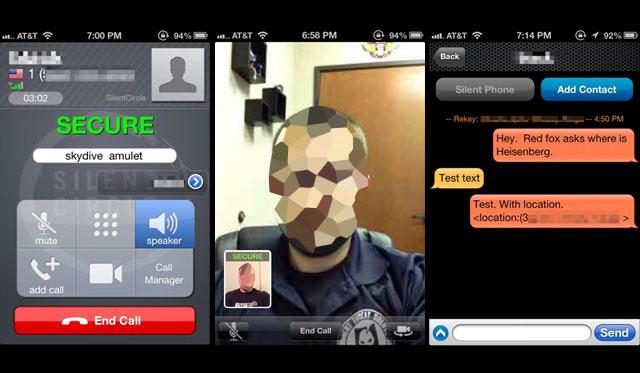
SilentPhone for Desktop works almost identically to Skype, and is stocked with many of the same features we’ve come to expect from a VoIP and video calling software suite. Users can securely call each other on an encrypted channel from their desktops, mobiles, or tablets (iOS and Android are both supported), as well as the option to phone out to regular landlines all from within the app.
Other features include the ability to send files of up to 100MB between two locations with an automatic “burn after reading” self-destruct mechanism attached, as well as a texting service that transmits protected messages between two devices at once.
International plans for voice start at $12.95 per 100 minutes, and scale downward accordingly when you purchase larger blocks of time in bulk.
BitLocker
Free, fast, and functional. While bells and whistles are nice if you’re picking out a new car, when it comes to securing the content of your digital life security itself takes precedence.
BitLocker is an easy to use utility that comes included as a part of the Windows architecture, available in Windows 7, 8.1, and XP. Though not activated by default, users of the OS can easily find out how to switch it on from the Help Center, and learn exactly how to run their own set of standard encryption tactics with the push of a button.
BitLocker has an advantage on most traditional software-based solutions in its use of what’s called the Trusted Platform Module network. Most motherboards you’ll find these days come pre-equipped with a specialized chip embedded in the board itself, disconnected from everything but the central hub, and capable of storing encryption keys completely separate of the traditional memory blocks or primary hard drive.
This means that even if malware does somehow find its way onto your computer, the TPM can block it from tunneling further without an explicit set of instructions first. The chip also features a series of triggers in place which, if activated, send a signal to the OS to divert any important files away from the infected partition, and re-scramble its entry code before the virus can cause serious harm to the core infrastructure.
If this type of expert protection sounds like something you need, head over to Microsoft’s Support website to learn how to set up BitLocker in three easy steps.
Iron Key
While encryption at home is easy to implement, what happens when you want to take that same sense of security with you on the road?
Say hello to Iron Key, a personal, portable, and nigh impenetrable storage solution that travels with you wherever you go. Capable of filing away any secrets you might pick up on that next business trip without the hassle of messy installations or downloads on a machine in someone else’s office, Iron Key is packed with a glut of helpful components that make it a much safer contender when compared to classical thumb drives.

Protected by a client-side digital certificate and a PKCS #11 interface, Iron Key is equipped with everything from 256-bit AES hardened file storage systems, to a highly-customized build of Firefox that will let you surf the net anonymously.
Iron Key comes in configurations of 2GB up to 32GB and costs around $109 for the base model and $599 for the deluxe all-in-one experience.
TrueCrypt (a.k.a CipherShed)
TrueCrypt is one of the oldest encryption applications available on the net and still one of the best. The company has proven throughout the past ten years that it’s a premier option for anyone looking to lock down their files on a budget.
When allegations surfaced that the company had been breached by an unknown group of hackers in November of last year, the team behind the open source software took to the web and called for any and all security enthusiasts to audit their program, a move which garnered a deserved restoration of faith among its millions of loyal users. Unfortunately, in May of 2014 the developers announced they would be ending support for the encryption method in anticipation of Windows XP losing its regular schedule of security updates from developers at Microsoft.
But then, after a miraculous show of support from the community, several of the software’s most fanatical members chose to fork off the effort, siphoning many of its best qualities and strongest protection methods into a new project, which they ceremoniously christened “CipherShed.”
The software utilizes many of the same pillars of privacy that made TrueCrypt the gold standard in personal hard drive encryption and has gone through the same rigorous open-source auditing process only to come out squeaky clean on the other side. The team claims that while CipherShed is similar to TrueCrypt from a foundational standpoint, much of what made its successor so good has been refined even further, and stripped down to the essentials to create a free, reliable way to encrypt your files at home.
Wrap Up
Last year an unknown, unassuming IT contractor for the NSA named Edward Snowden risked his life and his freedom so that we could be informed about what our government is up to behind closed doors.
In doing so, he lit a spark under the collective conscious about what it means to be truly secure in this uncertain age of rapidly evolving technology, and taught us that no matter how safe we think we are, there’s always going to be someone out there seeking an exploit – and it’s not always the people we think of as “the bad guys.” These four tools will help protect you from anyone seeking access to your most private files.


