Many of us go about our day, logging into online accounts from home, work, the library, the Apple store, and wherever else in order to read that inspirational story Mom e-mailed us about a kitten befriending a dog, and everything is hunky dory. Someone, on the other hand, is currently becoming the person you read about who had their password stolen, and their bank account hacked using the information they e-mailed themselves “that one time.” (Almost two thirds of all Americans have been affected, according to a study from Internet security giant Symantec. This type of digital information theft is easier than many of us realize.)
Security concerns have grown steadily over the last several years as users continue to put more and more private data behind the security vault door that is a Google account login. But perhaps these concerns are finally being laid to rest. Google is rolling out a new solution for those desiring additional protection that will make Google as the Alfred to your Bruce, the M to your James, the home base secret-keeper to your mobile, private data-accessing lifestyle.
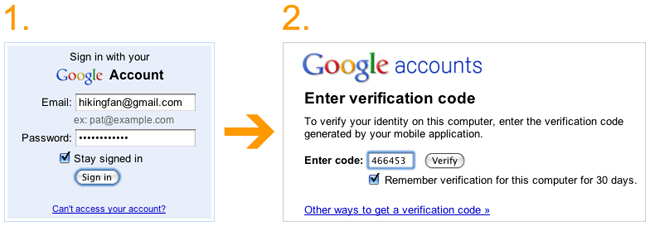
You can now activate a “two-step verification,” which will will require you to login with your username and password as usual, and then, on a second page, fulfill a request for a verification code before admitting you to your account. This verification code, randomly generated by Google, is only valid for the few seconds while you are completing the login process, and provided to you upon your request. Anyone who steals your password, or even this secret code, will not be able to login to your account later and steal all of the details of your “girls night out” planned for next Thursday night.

To ease the burden of this process for the numerous times a day you access your Google account, you can input a one-time authentication code for devices you use all the time. A little trickier is the requirement to generate and store app-specific pass-codes for programs like Apple Mail and iCal, which often automatically login to your Google account and regularly pull down new data for your preferred method of interface.
We’ve been on the old username-and-password system for some time now, but this new, second-tier authentication approach is starting to spread. You may have seen it on bank websites, with their periodic prompt of security questions, or a “call and answer” system with unique images tied to your account, so that you can verify the page you’re on before inputting your password. You may even have received a portable, random password-generating key fob for your corporate or securities-trading account. Yahoo has taken steps to protect users by helping team them up with Norton’s Internet Security product.
We can’t say your information is now invulnerable, but Google, as usual, has taken another promising step towards solving a big consumer problem. Google’s Accounts Help Center has details on how to get your own Google account set up with two-step verification.



