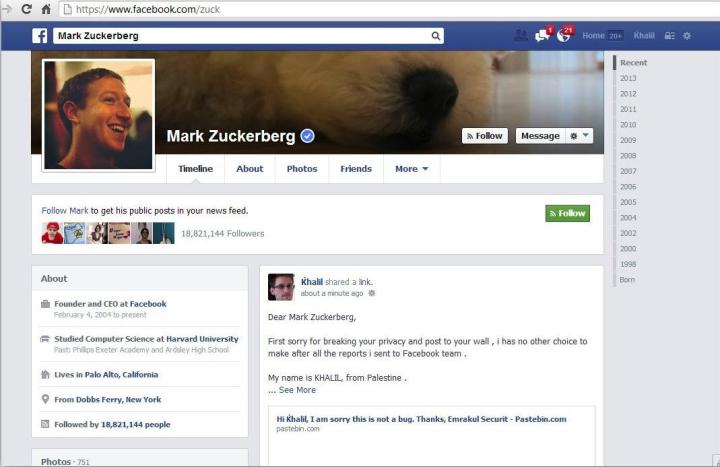
You often hear stories about how a hacker breaks into a business’s website, then the company ends up hiring said hacker as some sort of consultant to prevent future attacks. For some reason, we doubt Facebook is going to take on Khalil Shreateh, an IT researcher from Palestine, after he hacked into Mark Zuckerberg’s wall to prove his security bug report.
Let’s be fair, we’re sure Shreateh had good intentions. Earlier this month, the researcher discovered a bug that allowed him to post on any user’s Facebook wall regardless of privacy settings. He even tested the vulnerability on Sarah Goodin – one of Zuckerberg’s Harvard friends. After reporting the bug to Facebook, the company’s security engineer identified as Emrakul did little to help, only replying in one sentence responses. “I dont see anything when I click link except an error,” wrote one email. “I am sorry this is not a bug.”
Frustrated, Shreateh felt he had to choice but to prove his point on the Zuck’s wall, hoping that by reporting to the CEO directly, someone will address the security flaw. “First sorry for breaking your privacy and post to your wall , i has no other choice to make after all the reports i sent to Facebook team,” Shreateh wrote, before providing descriptions and links to the issue. As if the matter wasn’t comical enough, Shreateh’s profile photo is a picture of Edward Snowden.
Shortly after the post, another Facebook engineer named Ola Okelola contacted Shreateh for more details. As a result, Shreateh’s Facebook was temporarily disabled as a “precaution,” and Okelola explained to Shreateh that his report did not contain enough technical information for the team to take action. Facebook also said it cannot pay Shreateh a reward since he exploited the vulnerability, thus violating the site’s terms of service.
“We get hundreds of reports every day,” a Facebook engineer commented on Hacker News, noting that the bug had been fixed since last Thursday. “Exploiting bugs to impact real users is not acceptable behavior for a white hat [report].” The company does admit, however, that the first engineer should have followed up and asked Shreateh for more details – so it looks like the whole situation was just a case of two completely misguided IT men.
Editors' Recommendations
- Mark Zuckerberg: Facebook made ‘operational mistake’ before Kenosha shooting
- Facebook bug caused valid coronavirus articles to be marked as spam
- Watch Live: Mark Zuckerberg testifies before Congress about Facebook Libra
- Mark Zuckerberg is in Washington to get more friends for Facebook
- Facebook’s new oversight board could overturn Mark Zuckerberg’s decisions
