- Home
- (in)Secure
(in)Secure

WPA3, the third generation of Wi-Fi security, has one giant flaw: You
Wi-Fi security will get a lot better with WPA3, but it's not going to change things overnight. Even when all of the hardware and software has been upgraded to support it, there are still going to be some glaring problems. Hackers know the best way to break wireless security and it's usually through the user.







Pay-n-pray cybersecurity isn’t working. What if we just paid when it works?
Companies and individuals sink loads of money into cybersecurity each year, and yet with each passing month, the situation seems to worsen. We spoke with a former NSA expert about a new approach to cybersecurity that could keep individuals much more aware of how they were being protected.

Facebook wants to own your face. Here’s why that’s a privacy disaster
We all love using facial recognition technology in services like FaceID or Windows Hello. But it has a serious dark side too. We spoke with a former White House official who has some legitimate concerns with what companies like Facebook is doing with it -- and how it’s being secured online.

People are reading your email. Here’s how to make them stop
The contents of your email are no private, at least not to third party applications that connect to Gmail. Considering what happened with Facebook and Cambridge Analytica, that should worry you. Follow these instructions to see exactly who is reading your email and how to turn them away.

After 14 years, a new generation of Wi-Fi security is coming. Here’s what to know
WPA3 is a new security standard for Wi-Fi hardware that will charge manufactuters with meeting stricter guidelines to be certified to support it. It will bring about greater security and privacy for users in the home and when utilizing 'open' public Wi-Fi networks, as well as better password protections for everyone.

Improving security means killing the password, but that battle has just begun
As much as password reuse is a problem because people use the same passwords for different sites and services, some think that storing passwords in a central location is a bigger problem. As we begin to move beyond password use altogether, do we need to reconsider how our login credentials are stored as well?

Why Mastercard is ripping a page from Bitcoin’s book
Mastercard wants to use the inherent security of blockchain to make money more intuitive and less hackable. Its new blockchain patents seeks to put an end to credit card skimmers. Regardless of what you think about cryptocurrency, the largest financial institutions are transforming real money to be more like it every day.

Apple’s new privacy features are bad for Facebook, but great for everyone else
At WWDC this year, Apple announced several new privacy and cybersecurity features, specifically in its Safari web browser. Apple didn’t shy away from naming names. It had Facebook right in its crosshairs. Here's how Apple is making a case for its more secure ecosystem, blocking Facebook in the process.

Duck, cover, and reboot your router? Why the FBI’s new warning is no joke
The FBI has discovered up to 500,000 home or office routers could be vulnerable to a dangerous cyberattack. According to experts, there are a couple of important factors that make this malware an unprecedented situation. But can resetting your router really prevent a major cyberattack?

IBM banned USB drives. Is it the future of security or a knee-jerk reaction?
With the implementation of the GDPR, more companies than ever are looking to better protect their data and that of their customers. But are they going about it in the right way? Kingston believes that the recent announcement of IBM's outright ban on physical media isn't taking the right tack in protecting digital information.

You’ll never read Facebook’s new data policy, so we did it for you
Facebook’s new data policy is 4,200 words you’re never going read, but the company has become a little more transparent about how they track users and non-users as they click on different pages and use other apps. Here’s everything you need to know.

Web trackers aren’t just spying on you; they’re slowing you down
As the world becomes increasingly aware of the privacy concerns of modern life online, anti-tracker extension maker, Ghostery, has drafted a new study that looks how a major component of many online services – trackers – could be doing more than invading users privacy: they might be slowing down the internet as we know it too.

Facebook’s very, very sorry, and it has absolutely no intention to change
Facebook’s F8 developer conference saw the company and its CEO, Mark Zuckerberg, discuss new features like Dating and Clear History. While lip service was given to issues like data security and privacy, few good solutions were offered. That should be no surprise given Facebook’s history with Cambridge Analytica, and many others.

It took them 15 years to hack a master key for 40,000 hotels. But they did it
Security research firm F-Secure announced that it had uncovered a massive security vulnerability affecting millions of electronic locks worldwide. We sat down with the researchers who discovered the exploit to discuss how its discovery may have made your next hotel stay a whole lot safer.

Cambridge Analytica’s ex-director wants to fix data privacy. Can we trust her?
Brittany Kaiser, the former director of Cambridge Analytica, is now partnering with a initiative called IOVO, or the Internet of Value Omniledger. She wants to pioneer a new understanding of data privacy, but can someone who abused data in the past really be trusted with the internet's future?

Cryptojacking is the new ransomware. Is that a good thing?
Malicious cryptominers and cryptojacking is a hot new malware trend that's been sweeping websites and victim systems for many months now. They've become so prevalent that ransomware is far less of a concern to consumers and businesses, but does that mean the new kid on the block is here to stay?

Your ISP can peep on your browsing, so Cloudflare is pulling down the shade
In a world still reeling from the Cambridge Analytica revelations, Cloudflare has introduced a new privacy-first DNS resolver called 1.1.1.1. It claims to make the internet safer – and faster.

Firefox is on the front line in the fight to protect your privacy
How do browsers handle the Meltdown and Spectre flaws, as well keep user data as secure as possible on social networks? We asked Dave Camp, Vice President of Engineering at Firefox, for his insider insight.

Facebook was always too busy selling ads to care about your personal data
Ultimately, the Cambridge Analytica scandal happened because Facebook has always cared more about selling ads than protecting your personal data. When you sell four billion dollars in ad revenue each year, it takes some effort to ensure that people’s data is protected.

Nowhere is safe now that AMD has suffered its own Meltdown
The public disclosure of flaws in AMD processors caught the company, and security researchers, off guard. They expose hardware some had come to regard as the PC’s last safe harbor.
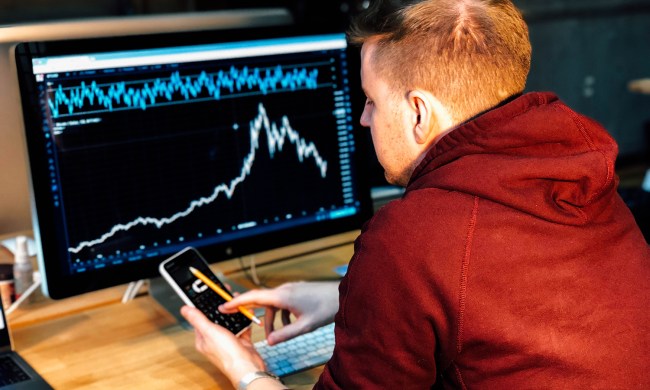
Cryptojacking turns your PC into a Bitcoin mine, but you won’t see a cent
Cryptojacking is the newest trend in malware, allowing hackers to steal your CPU power to mine cryptocurrency. Here’s how the biggest websites on the internet have been hacked — and what a future dominated by it could look like.

How Google’s ‘Project Zero’ task force races hackers to snuff out bugs
They discovered the Spectre and Meltdown security flaws before anyone else, and made sure Intel was staying honest in how it reacted. Unfortunately, the Project Zero crew aren’t the only ones searching for bugs.

Did I do that? Intel is going to make a killing fixing its own Meltdown
Intel dropped the ball on Meltdown and Spectre. Now, it’s poised to profit off of its decision to sell critically flawed products to an unwitting populace.




