This is a word that’s been tied to Edward Snowden, The Silk Road, and Bitcoin. Even the NSA made the front page with its very own PowerPoint presentation on the many challenges it faced while trying (and failing) to crack its elaborate code. What is Tor, where did it come from, and why can’t people stop talking about it?
What’s a Tor?
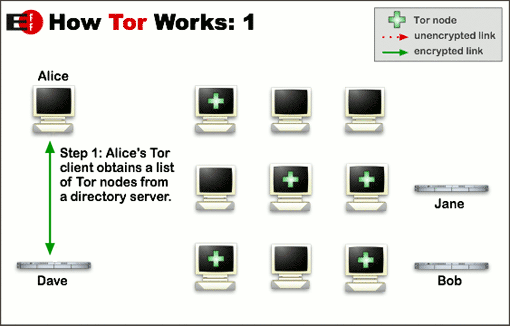
Tor, (short for “The Onion Router”) was initially launched in 2002 by a small team of anonymization enthusiasts who were looking for a new way to connect with each other without relying on the standard routers that were available to the public. The network is based off technology that dates back to the mid-1990’s, developed by the US Naval Research Laboratory in conjunction with DARPA as a method for sending classified documents between agencies over the backbone of the early internet.
Tor works by creating a series of relays in what’s known as a “meshnet.”
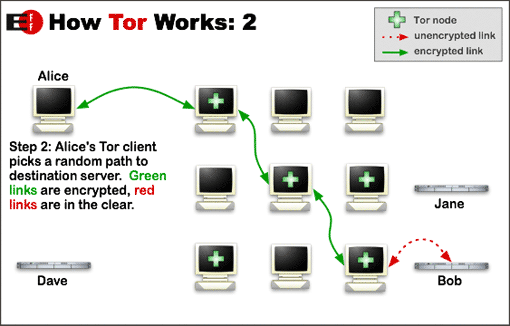
To put it simply, Tor works by creating a series of relays in what’s known as a “meshnet,” a collection of nodes run by anyone who wants to support the service that jump from one to the other in random succession. Each link in the chain is completely untraceable from the last, and depending on your preferred level of protection (and tolerance for a slow connection), your search queries, website visits, and communications can hop from as little as three to as many as 50 different locations around the globe before they successfully transfer from sender to receiver.
It’s these gaps that make the traffic especially difficult (and some would argue impossible) to track. Because the information is split up into thousands of individual packets that each enter and exit from different servers, it takes an excessive amount of time and energy to find the source or the intended recipient without a hefty chunk of know-how and ingenuity on behalf of your would-be surveiller.
So, now that we know how it works, what exactly can we do with it?
.Onions
Right out of the gate you should know you can’t visit any old website while attached to the Tor network.
Because many of our favorite portals still use a litany of hidden cookies, browser data, and logging software to figure out who we are, what we’re doing, and how that information can be monetized for advertisers, Tor connects to a different part of the web, known as the “dark web.”
This is not to be confused with the “deep web,” which is primarily made up of servers full of corporate data that Google doesn’t index for general viewing. Instead, the dark web is a series of destinations known as “onions,” which can be anything from the aforementioned online drug markets (“The Silk Road” might ring a bell if you keep up on these kinds of things), to something as simple as a list of resources that people can rely on for fully encrypted communications.
Other useful .onions include the mainpage of WikiLeaks, the encrypted messaging app TorChat, and the popular privacy-focused search engine DuckDuckGo.
In the interest of keeping these sites functional and out of the public eye we won’t be revealing their exact addresses in this article, but they can easily be accessed by heading over to the Tor Onion Wiki on the project’s website here.
Nodes
When you try to connect to Tor you’ll find its software offers two different ways to connect to the mesh. You can either let the system automatically choose your entrance and exit “nodes” (the servers that handle traffic) for you, or you can custom select which locations fit your needs best and cherry pick from there.
There’s still a number of rough edges that need to be ironed out if it’s to become a fully trustworthy way to keep your identity safe online.
Granted, you should be very careful while selecting the nodes you use and the nodes that are tossed aside, as just a few weeks ago members of the infamous hacking collective Lizard Squad took control of around 3,000 exit relays using a zero-day they’d discovered while breaking down the internal code.
Of course, they themselves use the service for everything from coordinating attacks to sending files between countries, so shortly after proving their concept they contacted the dev team behind Tor to work on a solution that would strengthen the network and prevent the mishap from becoming a bigger problem in the future.
Firefox
As it stands, all versions of Tor still need to glom onto the Firefox browser in order to work properly. The basic Tor installation comes with its own customized build, but you can also use your own browser with an extension to run it without a hitch.

Be forewarned that this is not exactly recommended, as your Firefox installation will probably have data that could be used to link you to a node (namely the bits and bytes held in Java). Still, this is a viable option if you don’t want to go the extra mile of installing a new Tor-specific browser.
Tails
Finally, for seriously devout privacy advocates, there’s Tails. This open source operating system based loosely on Linux modifies the entire operating system to create a hardened, encrypted OS that fits snugly on a USB stick.
It’s a similar concept to what we saw from the Windows-To-Go system from Iron Key; custom thumb drives created to encrypt your data and movements no matter where you are in the world.
For those who want a one-stop, no-hassle way to ensure that all of your personal data and information is as safe as possible from prying eyes, Tails OS is a perfect way to wrap everything you do into one tightly knit, almost untraceable package.
Conclusion
Tor is an excellent option if you’re concerned about privacy, want a secure, discreet way to communicate with friends, and have a rudimentary knowledge of how the Internet works. It’s not flawless, and there’s still a number of rough edges that need to be ironed out if it’s to become a fully trustworthy way to keep your identity safe online, but for now it’s the best bet we’ve got and should be a staple addition to anyone’s toolkit who values personal privacy above all else.
To get started with Tor you can visit the project’s website for a detailed breakdown of the instructions you’ll need to get things rolling in the right direction.
Editors' Recommendations
- Here’s how you could protect your RTX 4090 from melting
- Twitter Circle is coming soon. Here’s what you need to know