China’s hacking the United States, according to an expose from Mandiant, which blew open the doors and tracked a network of hackers’ activities down to the very building. The report is an intriguing and straightforward read with few terms laymen would have to look up in a dictionary. If you’re trying to find the source of the report, here it is straight from Mandiant’s website. Otherwise do not, and we can’t stress this enough, do not open up suspicious emails.
There have been reports of phishing popping up in the news recently, what with Twitter, Pinterest, and Tumblr user’s email addresses mined by hacker. Phishing is an age old tactic since the dawn of email, but hackers have been getting increasingly clever with their tactics. Hackers don’t always need to be computer whizzes. Social engineers, who use social duping tactics, can use the right phrasing to sound like a legitimate entity, only to steal your information. Using both hacking skills and these social duping methods, someone is reportedly circulating a false Mandiant report that’s dropping Trojans onto victims’ computers.
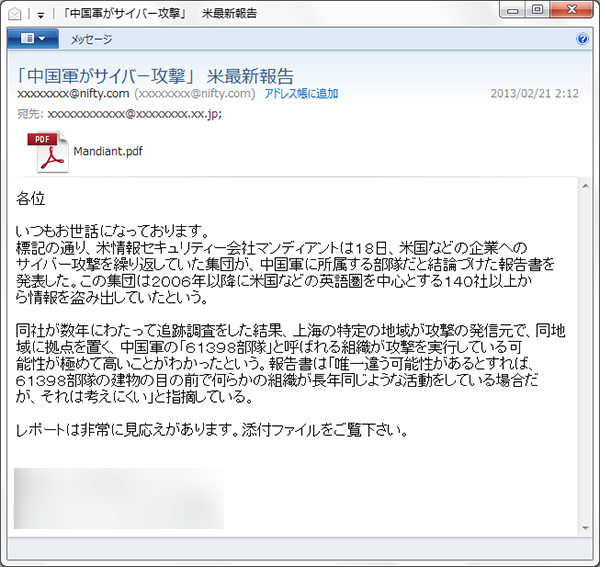
Symantec says that the email sender claims to be from the press, who is recommending users to read the attached report. And by the looks of it, the report appears legitimate from a glance, thumbnail and all. The language of the email, based on the screen shot that Symantec displays, is in Japanese, and notes that the email may be sent in various languages. But here are a couple of pointers to ID the suspect email that Symantec points out: “Like in many targeted attacks, the email is sent from a free email account and the content of the email uses subpar language. It is obvious to a typical Japanese person reading the email that it was not written by a native speaker.”
Surprise, surprise, the delivery platform this hacker has decided to use is Adobe. When the victim opens up the attached PDF in the email, their computer is immediately infected. “The PDF file may drop Trojan.Swaylib and Trojan.Dropper, which drops Downloader,” Symantec researcher Joji Hamada writes. In some instances the Trojan masquerading as a PDF will drop malware.
Does this situation ring a bell? Just two weeks ago, Adobe had a zero-day exploit on their hands that would drop two DLLs (dynamic link library) onto the victim’s computer and would trick the computer into running malware. Well Adobe claimed to have patched that issue up, but with all of Adobe’s faults with Acrobat and Reader, it isn’t shocking that another vulnerability is being exploited.
Editors' Recommendations
- You can use Microsoft Teams to send text messages. Here’s how
- Here’s how you can win this insane, custom Starfield PC
- This GPT-powered Discord bot can teach you a new language — here’s how to use it
- No, 1Password wasn’t hacked – here’s what really happened
- Here’s how you can get The Last of Us for free from AMD

