
Destructive hacking group REvil could be back from the dead
Ransomware gang REvil was unceremoniously shut down in 2021, but the group’s website is back up and running, suggesting the hackers could be back in action.

Chinese hackers use VLC media player to launch cyberattacks
According to a recent report, a famous Chinese hacker group was able to combine VLC Media Player with a dangerous exploit, deploying malware to users.

The dark web’s biggest marketplace just got taken down
The dark web just got a little less darker: The biggest dark web marketplace in the world, Hydra, has been taken offline.

Victims of latest massive LAPSUS$ hack include Facebook, DHL
Hacking group LAPSUS$ has revealed its latest target: Globant, an IT and software development company whose clientele include the likes of tech giant Facebook.

Not even your PC’s power supply is safe from hackers
Hackers have managed to find a way to successfully gain access to uninterruptable power supply (UPS) computer systems, according to a report from CISA.

Microsoft has a warning about working in the metaverse
In a blog post, Microsoft talks about the risk of working in the metaverse and the steps that can be taken to secure it

What is email spoofing?
Attempts at online theft often start with a phishing scheme -- and phishing attempts often rely on email spoofing. Here's how spoofing works and how to spot it.

Google makes important Workspace change to prevent phishing
Google changes the way email notifications work when you collaborate in Workspace apps to prevent phishing attacks.

Hackers stole top-secret GPU details — then Nvidia hit back
After a cyberattack that took Nvidia’s systems offline, the hacking group behind the breach has revealed it has acquired over 1TB of data from the tech giant.

Unprecedented cyberattack takes Nvidia offline for two days
The culprit behind a recent cyberattack on U.S. chip-maker Nvidia is still at large. The breach took Nvidia's systems offline for two days.

This MacOS Trojan stealthily lifts your data, says Microsoft
Microsoft has exposed a Mac trojan known as UpdateAgent that can stealthily lift your data.

Researchers say your GPU could expose private info online
As if online privacy was not difficult enough to achieve, a team of researchers has now found that users can be tracked just by analyzing their graphics cards.

Microsoft stopped the largest DDoS attack ever reported
Microsoft mitigated a DDoS attack on an Azure server in Asia with a throughput of 3.47 Tbps, making it one of the largest attacks in history.
Apple paid a student $100,000 for successfully hacking a Mac
Apple has just paid over $100,000 to a curious student who attempted to hack the camera on a Mac -- and succeeded. He shared the process in a blog post.

Cloudflare reports a massive 175% increase in DDoS attacks
Cloudflare has just released a report detailing DDoS attacks from the last quarter of 2021. The last half of the year saw a massive increase in ransom attacks.

The best free VPN for 2022
Getting the protection of a VPN doesn't have to cost you an arm and a leg. There are many free options that will keep your data safe while helping your budget.

Update your Mac now to fix vulnerability that gives full access to spying apps
Microsoft is warning of a new Mac vulnerability that could allow attackers to secretly hijack apps and spy on you.

Now’s your chance to get McAfee Total Protection for up to $100 off
Get up to $100 off McAfee's Total Protection suite. Antivirus protects your devices, a VPN secures your privacy, and identity protection covers the rest.
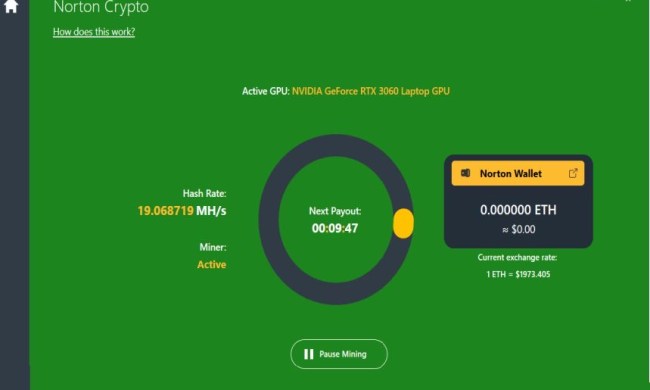
Norton has a crypto miner for PCs that can’t be easily uninstalled
Norton recently launched its new Crypto feature, allowing users to mine Ethereum while their PC is idle, but it’s already drawing ire from regular users.

Are you using one of these passwords? If so, it’s time for a change
NordPass has revealed the most common passwords used in 2021, confirming that “123456” remains the most popular password for the second year in a row.

The smart home hacking scene in Scream is possible, but you’re probably OK
Smart home hacking is possible but very, very unlikely. There are some steps you can take to stay safe.

Hackers just stole personal data from millions of Acer customers
Acer has suffered from a second disastrous data breach in 2021. A group of hackers breached Acer's servers and stole over 60 gigabytes of user data.

Update your AMD Ryzen drivers now to avoid password leaks
A report from a cybersecurity firm exposed a critical security flaw in all AMD Ryzen chipsets. Here's how to protect yourself.

GPUs could become Trojan horses for future cyberattacks
Malicious code was allegedly shown to have the ability to run on a GPU's VRAM in the latest proof-of-concept hack sold on the black market to hackers.

Protect your email now against the return of this nasty ransomware botnet
The infamous Trickbot ransomware botnet is on the rise again after being dismantled in 2020. Here's what you need to know to stay safe.

Update your Windows PC now to fix this critical PrintNightmare security flaw
A serious security flaw known as Print Nightmare is impacting Windows, and Microsoft has issued a fix for it. Here's how you can update to stay safe.

5 lines of code allowed attackers to wipe tons of data from popular hard drive
After a series of attacks last week, Western Digital says there's another exploit impacting My Book Live and My Book Live Duo hard drives.

The Navy wants you to hack into its systems. But of course, there’s a catch
Hacking into the U.S. Navy's computer systems is a surefire way to get yourself in trouble -- unless you do it during this upcoming hackathon.

How to tell if your security camera has been hacked
Security cameras can keep us safe, but they can also do the opposite if they're hacked. Here's how to tell if your smart home security camera is compromised.

Some ethical hackers are making huge amounts of cash
Some ethical hackers are using their skills to make huge amounts of cash as they help companies big and small to find vulnerabilities in their computer systems.

Tesla factories’ security cameras caught up in wider hack
A Silicon Valley startup offering cloud-based security camera services has had its systems breached in a major hack that accessed numerous live feeds.

Hacker tries to poison the water supply of a Florida city
A computer hacker tried to poison the water supply of a Florida city, local police revealed on Monday, February 8.

iPod hack puts 50 million Spotify songs in your pocket
When Apple launched the iPod in 2001, it went with the slogan “1,000 songs in your pocket.” Now someone has rebuilt it to increase that number to 50 million.
Are you using any of these browser extensions? Uninstall them now
Security firm Avast has identified 28 malicious Google Chrome and Microsoft Edge extensions that have received 3 million downloads globally.