The exploit in question happens when a hacker sends an MMS message containing a video that includes malware code. What’s most alarming about it is that the victim doesn’t even have to open the message or watch the video in order to activate it. The built-in Hangouts app automatically processes videos and pictures from MMS messages in order to have them ready in the phone’s Gallery app.
Updated on 08-25-2015 by Kyle Wiggers: Added news regarding patches for the AT&T variants of HTC’s One M8 and One M9. Jump to List of patched devices for more.
As such, a hacker could gain control of the device before the victim even knows about the text message, and even if phone owners find the message right away, there is nothing they can do to prevent the malware from taking over their device. The hacker would have access to all data and the ability to copy or delete, and would even have access to the microphone and camera, all pictures on the device, as well as Bluetooth.
Here’s everything you need to know about the hack, what’s being done to patch it up on all the affected Android phones, a list of all the patched devices, and what you can do to defend yourself while waiting for a patch update:
Click on a link to jump to a topic:
The first patches may not be enough
Google acted fast to combat Stagefright, pushing out updates to many of its Nexus devices and its OEM partners. Big-name companies like Samsung, HTC, and Motorola, quickly moved to send a patch to their users. As such, you’d be forgiven for thinking that the unprecedentedly broad security update would be enough to protect against Android’s Stagefright vulnerability, but that appears not to be the case. Researchers at security firm Exodus Intelligence say they’ve been able to bypass the fix with cleverly crafted malware.
The problem, said Exodus Intelligence, is a programming error within the update currently rolling out to smartphones. A malformed MP4 video file crashes even patched Stagefright libraries, leaving devices on which they’re running vulnerable to attack.
“There has been an inordinate amount of attention drawn to the bug — we believe we are likely not the only ones to have noticed it is flawed. Others may have malicious intentions,” warned Exodus in a blog post.
Google says a vast majority of devices — more than 90 percent — aren’t vulnerable to the workaround thanks to ASLR (address space layout randomization), a security technique in Android which automatically mitigates certain exploits. But the search giant says it’s already submitted a fix to OEMs and Android’s source code to resolve the issue, and furthermore plans to push out security updates to its line of Nexus devices in September.
List of patched devices
As initially reported by Ars Technica, updates that close the Stagefright vulnerability are available for a number of Samsung, HTC, LG, Sony, and BlackPhone handsets. If you see the update, go download it. Of course, the update may not be available from every carrier yet. So far, Sprint, T-Mobile, and AT&T subscribers have seen fixes.
Here’s a list of devices, organized by manufacturer, that’ve been patched so far:
- Samsung ‘s Galaxy S5, S6, S6 Edge, and Note Edge
- HTC’s One M7, One M8, and One M9
- LG’s G2, G3, G4
- OnePlus 2
- Sony’s Xperia Z2, Xperia Z3, Xperia Z4, Xperia Z3 Compact
- Silent Circle’s Blackphone
The problem is that most devices won’t receive the fix right away, if ever. Manufacturers are notoriously slow in providing updates, and the update process is further compounded by each mobile carrier’s lengthy internal testing before the software’s official release. Luckily, this time around, manufacturers seem to be taking the hack serious enough, and the ones that haven’t already released patches are working on them.
OnePlus announced in mid-August that version 2.0.1 of the Oxygen OS includes the patch for the Stagefright hack. This update is rolling out in India first, followed by other areas.
Motorola announced the Moto X Style (and Pure) and Moto X Play will already have the Stagefright hack security update when the respective phones are launched. The company will start sending patch updates to carriers for the following phones starting August 10, 2015:
- Moto X (1st Gen, 2nd Gen)
- Moto X Pro
- Moto Maxx/Turbo
- Moto G (1st Gen, 2nd Gen, 3rd Gen)
- Moto G with 4G LTE (1st Gen, 2nd Gen)
- Moto E (1st Gen, 2nd Gen)
- Moto E with 4G LTE (2nd Gen)
- Droid Turbo
- Droid Ultra/Mini/Maxx
Unfortunately, this does not mean the updates will be available to phones right. Motorola said there are over 200 variants of software and it will prioritize updates based on the largest groups of consumers first. Users will get a notification when the update is available to download and install.
Google announced that it is sending a patch for the Stagefright vulnerability out to all of its devices, including the Nexus 4, Nexus 5, Nexus 6, Nexus 7, Nexus 9, Nexus 10, and Nexus Player. The fixes have already shown up on some Sprint customers’ devices. Google stated that it will rollout security fixes to all Nexus devices once a month from now on, so that no Nexus devices languish without a serious bug fix.
The researcher who discovered the vulnerability, Joshua Drake, confirmed earlier the Nexus 6 was patched, but for only some of the issues. He praised Silent Circle for already updating the Blackphone, but the Nexus 6 and Blackphone represent a very small amount of Android phones.
Thanks @jduck for the kind words & reporting serious Android bugs. With your help, we patched Blackphone weeks ago! http://t.co/SmEGLfmVZM
— Silent Circle (@SilentCircle) July 27, 2015
HTC told Forbes that its patch will be distributed all users very soon: “Google informed HTC of the issue and provided the necessary patches, which HTC began rolling into projects in early July. All projects going forward contain the required fix.” The update’s rolling out to HTC’s One series.
After contacting ZTE, Digital Trends received the following statement regarding its plans to secure phones against the Stagefright hack: “We are currently developing a software update that will be available soon. Security is a top priority at ZTE and we are working with Google to resolve this issue as soon as possible.”
It is believed that all Android phones with Android 2.2 or higher are vulnerable to this attack. Considering there are more than 1 billion Android phones in use on the planet, it’s safe to assume that more than 950 million phones are susceptible.
How to defend yourself
A new app from Zimperium, the folks who discovered the flaw, will tell you if your phone is vulnerable to the Stagefright hack.
The Stagefright Detector app is as simple as it gets. After downloading and installing the app, simply launch it. The app will go through a list of common vulnerabilities and exposures (CVEs) that impact the phone. It will then tell you if you’re vulnerable or not.

If vulnerable, you will find a contact us option. This option won’t tell you how to fix the issue, but it is a way for Zimperium to anonymously collect information regarding the vulnerable CVEs specific to the device. The anonymous information will be shared with the Zimperium Handset Alliance, which includes 25 of the largest global carriers and device manufacturers as members. It could help carriers and manufacturers detect which devices need patches.
Click here to download the Stagefright Detector app from Google Play. If you find out that your device is vulnerable, there are steps you can take to protect yourself.
How to protect your device
It was initially believed there was no defense to the Stagefright MMS attack since Hangouts and the Google Messenger app auto-download videos, but there is a way to stop this from happening if your phone proves to be vulnerable from the Stagefright Detector app. By disabling an option called “Auto retrieve MMS” in your default messaging app, you can stop the video from auto downloading, thus stopping the malicious code from executing.
Most Android phones include both Hangouts and another SMS/MMS Messaging app that is the default app out of the box. Each manufacturer offers their own version so it might be called Messages, Messenger, or something similar.
If you’re a Hangouts user, you were given the option to set it as your default SMS/MMS messaging app upon first opening the app. Setting Hangouts as the default generally overrides the other pre-installed app.
You will need to make the change in the app that you set as your default messaging app, which is the app that you use to send and receive SMS/MMS messages on a daily basis. If it happens to be Hangouts, we recommend that you also make the change in the other app as well because messages are sent to both apps on some older phones. If it’s a newer phone, the settings for that particular app might be grayed out, which means that it isn’t receiving duplicate messages.
We know it sounds complicated, but the bottom line is that if the option is there, change it. If not, then you’re okay.
How to turn off “Auto retrieve MMS” in Hangouts
- Open the Hangouts App, and tap the hamburger menu (three lines) at the top left next to your name on the main screen.
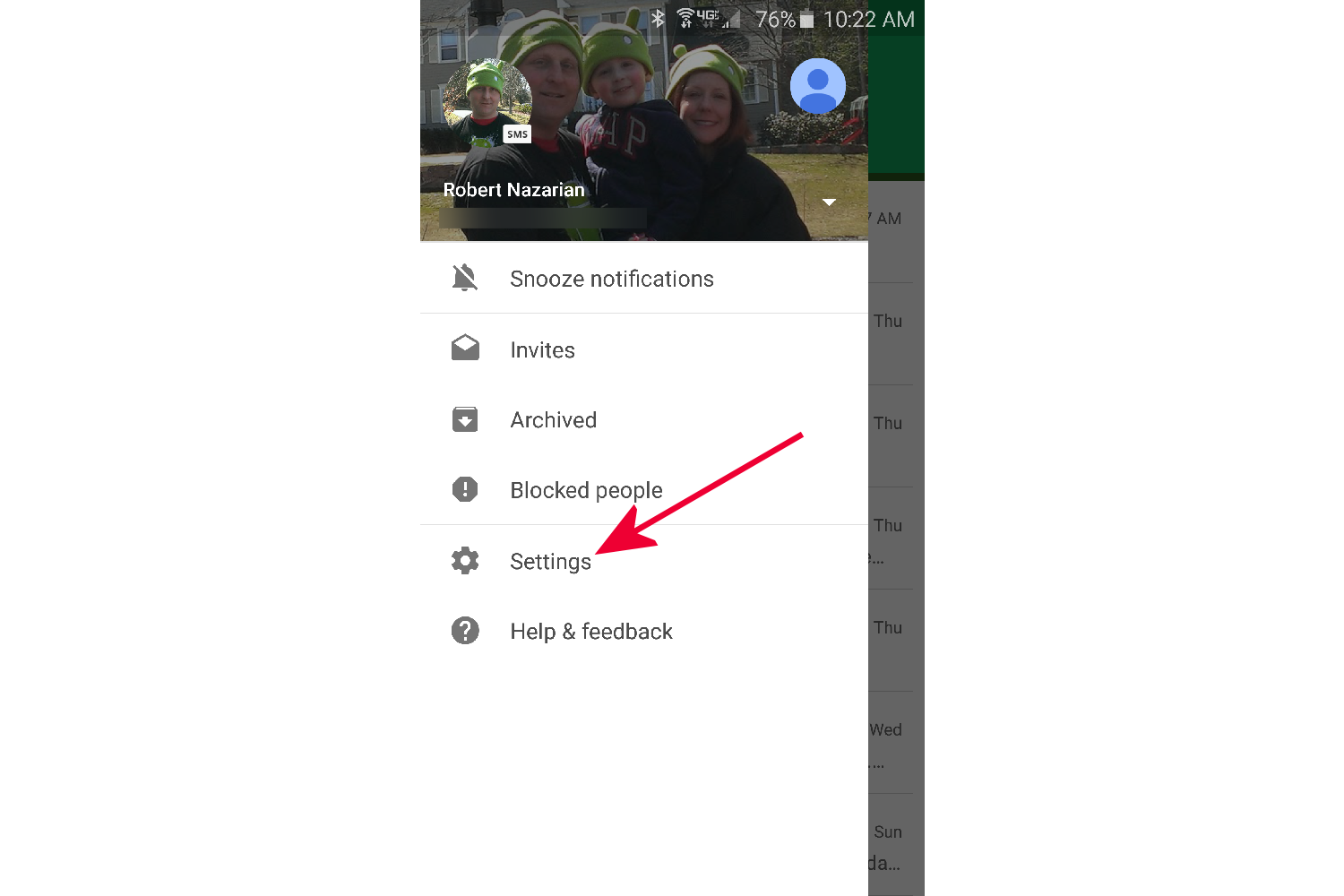
- A pop out menu will appear from the left side. Tap on Settings.
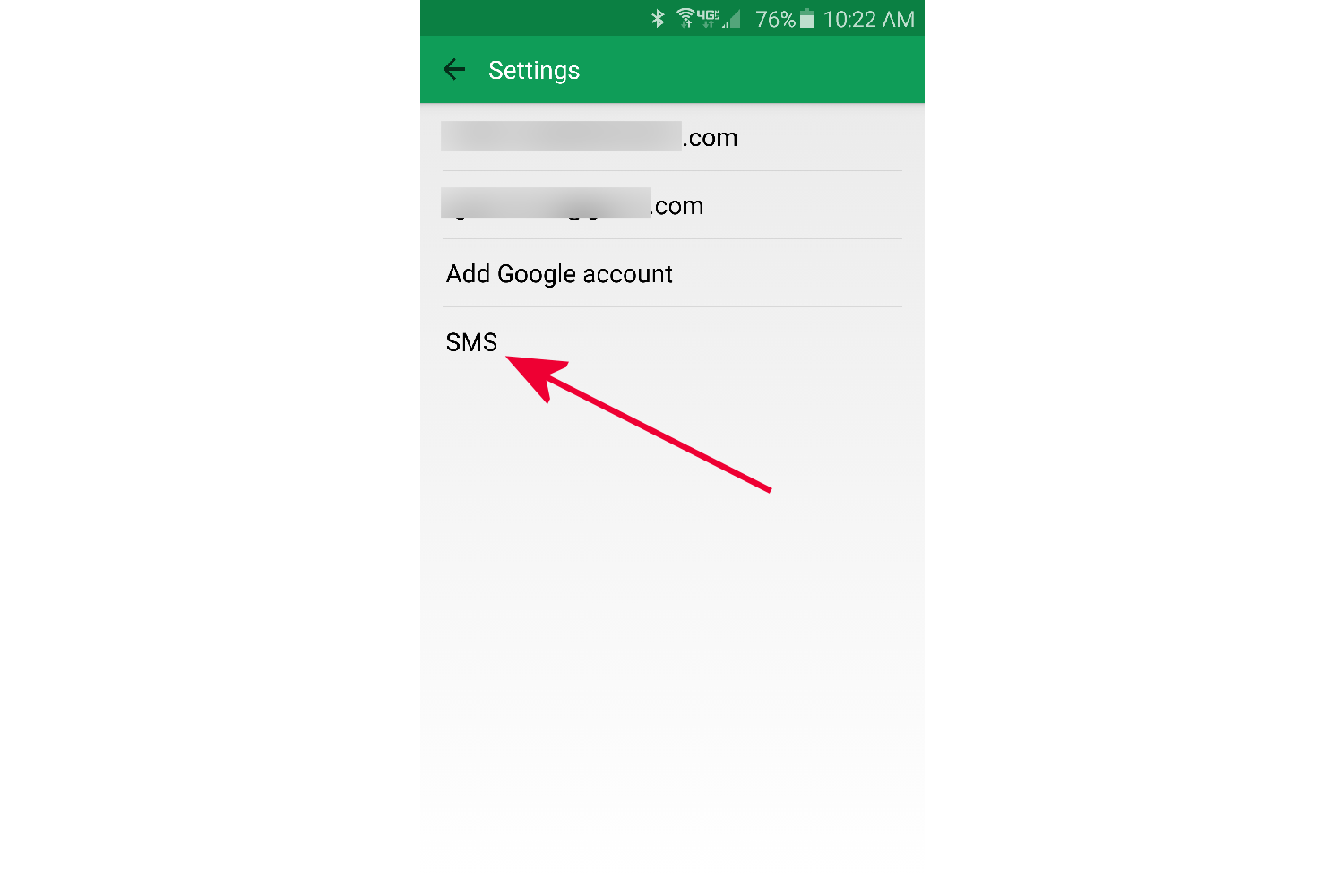
- Tap on SMS.
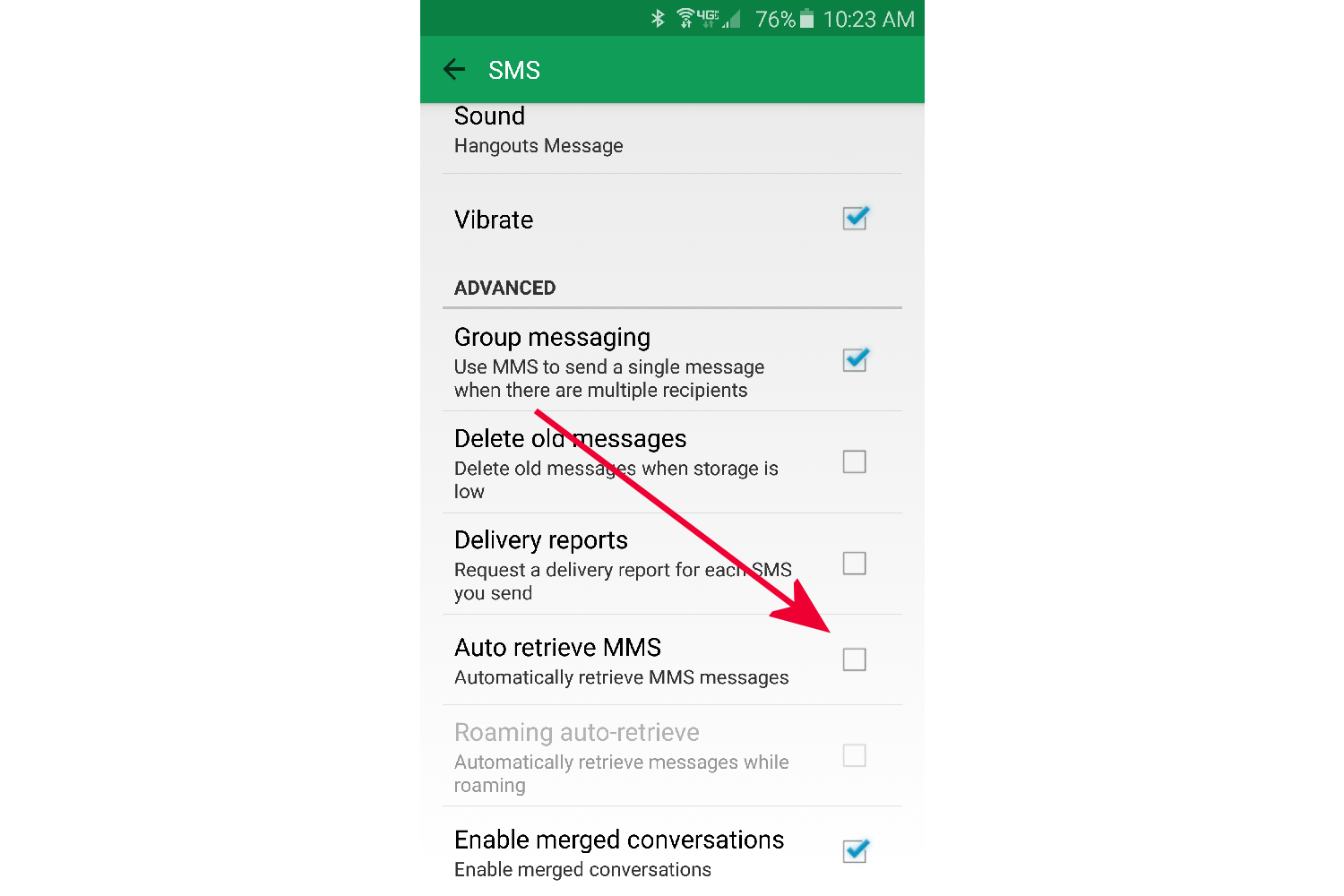
- Scroll down to Auto retrieve MMS and uncheck it. If the option is grayed out, then Hangouts is not your default SMS app, and you need to follow the next set of instructions below to turn it off in the other messaging app that you use for all your SMS messages.
How to turn off “Auto retrieve MMS” in Messaging apps
This example will be the Messages app on the Samsung Galaxy S6 and Galaxy S6 Edge. You will find a similar app on other phones, and although the menus won’t be the same, the steps will be very similar. The bottom line is that you need to find the Settings for the app.
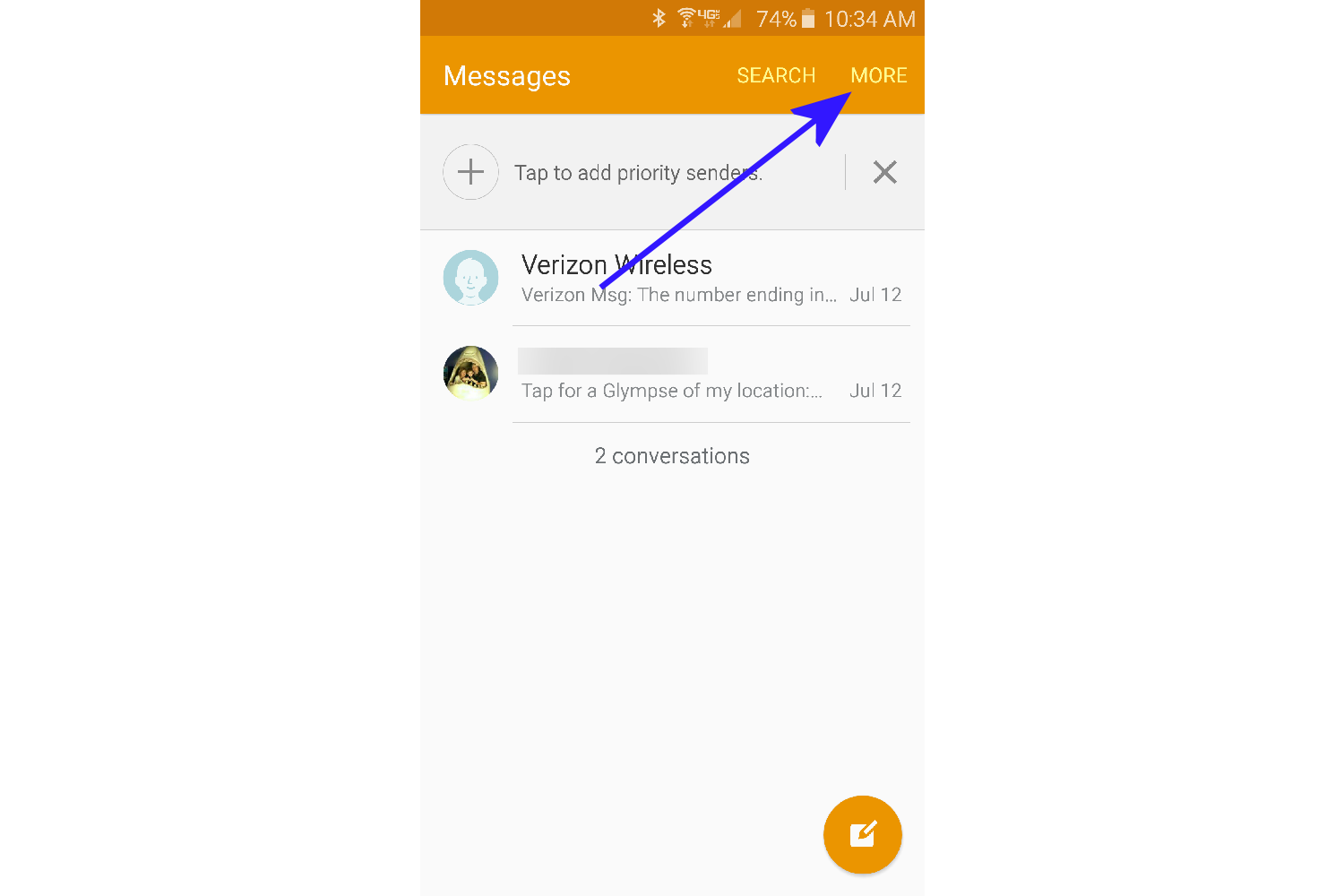
- Open the Messages app (Galaxy S6/Galaxy S6 Edge), and tap on More at the top right.
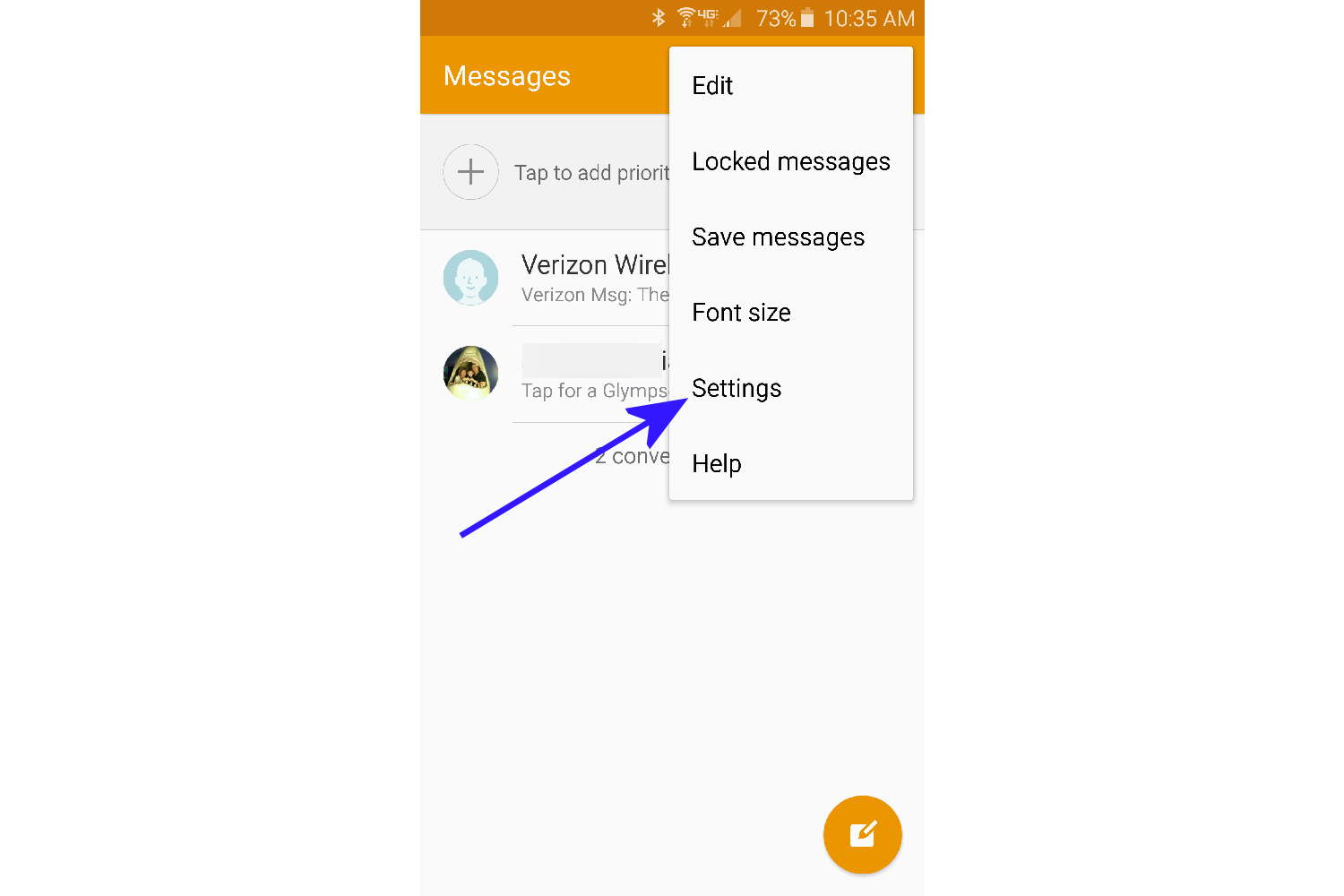
- A pop out menu will appear. Tap on Settings. Note: If this option or any of the below options are grayed out, then Hangouts is your default messaging app, and you need to make sure to follow the above instructions titled, How to turn off “Auto retrieve MMS” in Hangouts.
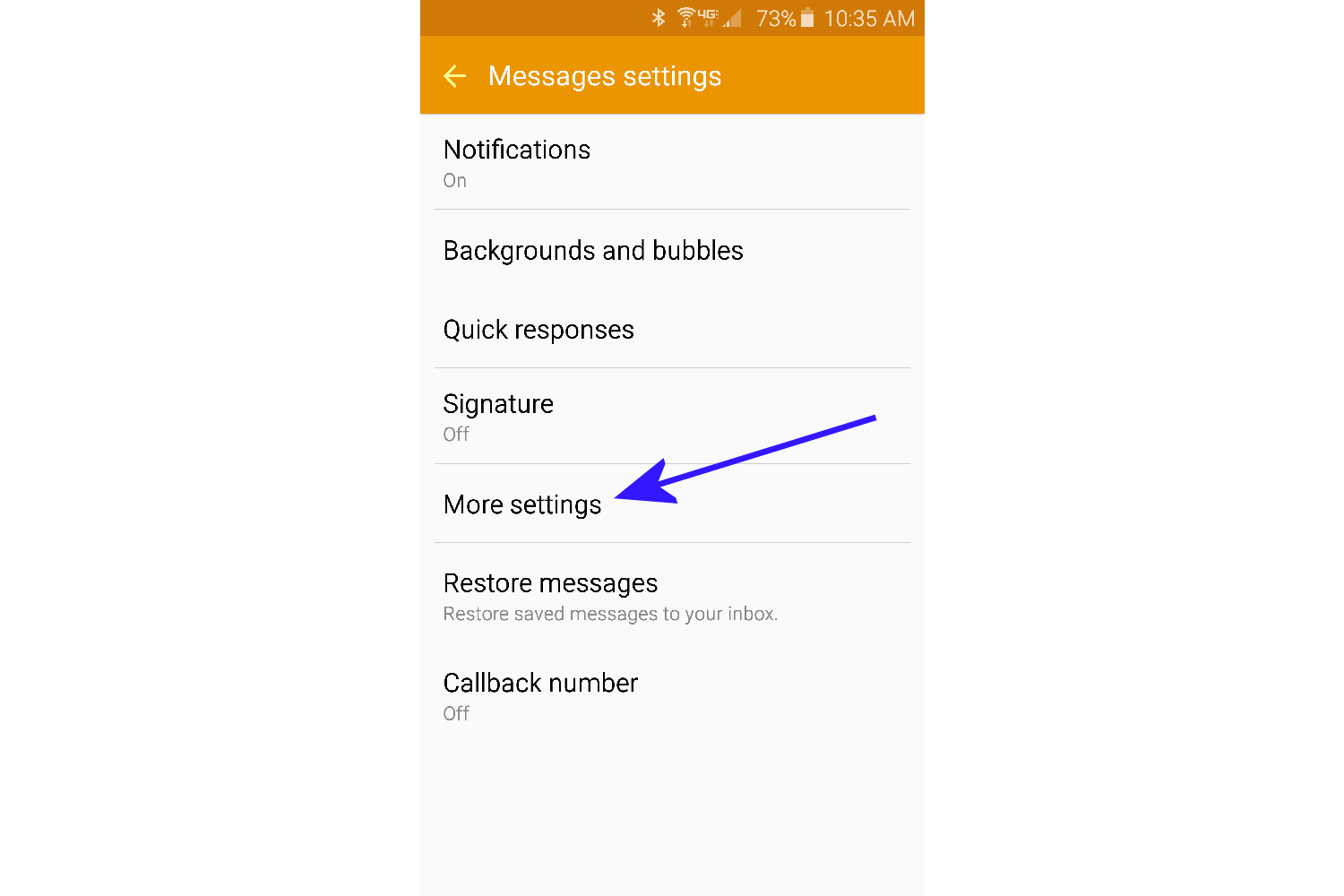
- Tap on More Settings.
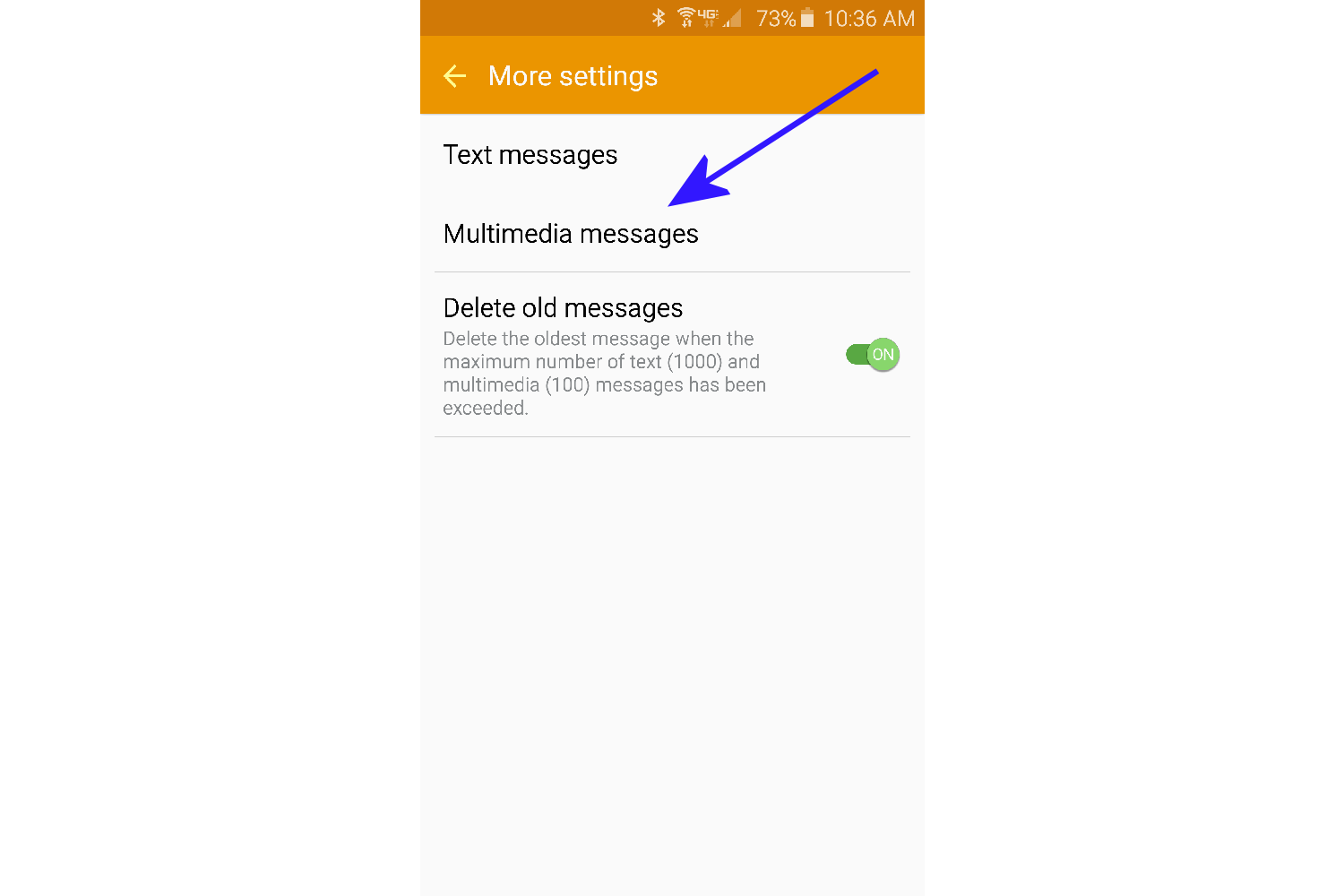
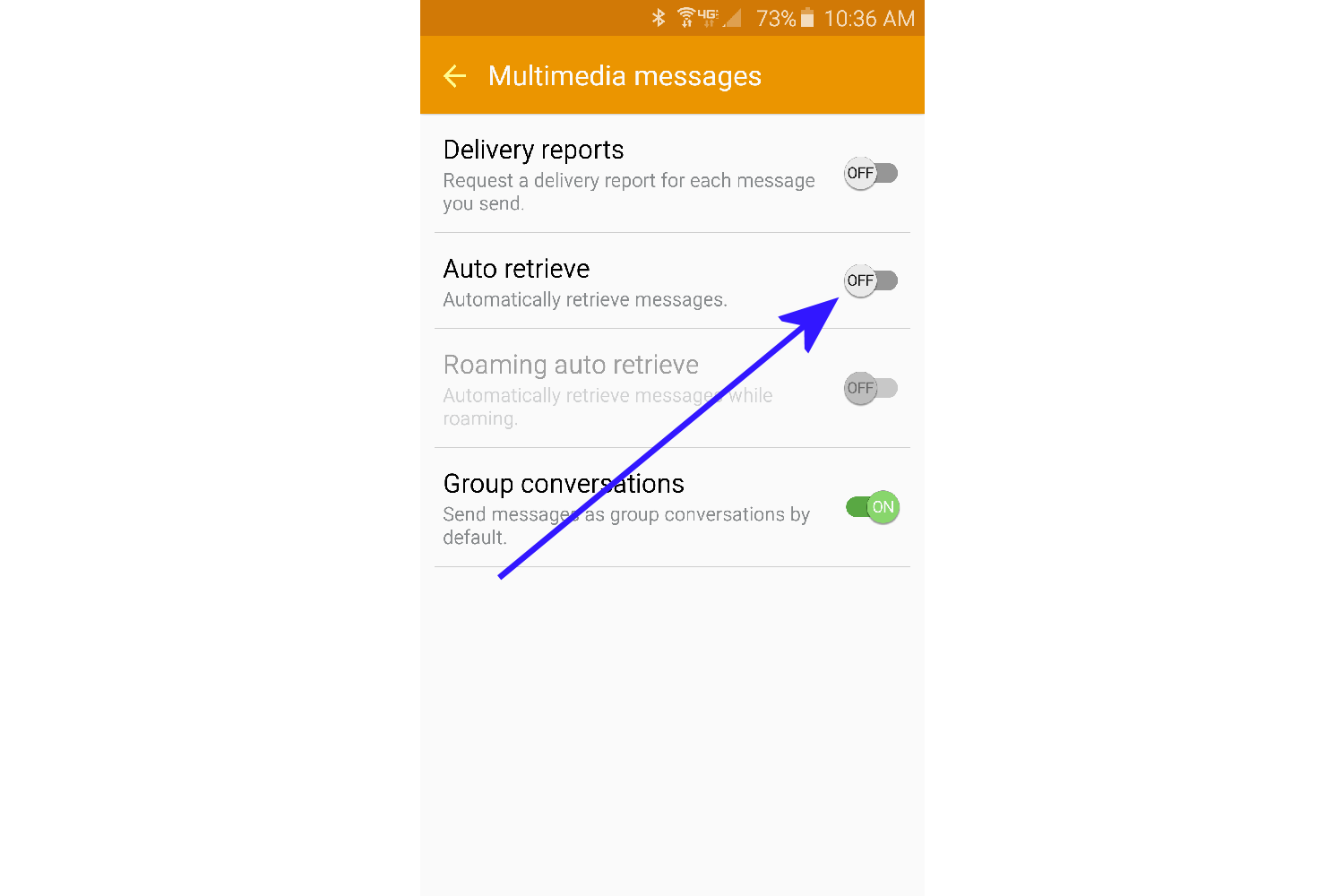
- Tap on Multimedia messages.
- Turn off Auto retrieve.
One you have made the change, videos will no longer be auto downloaded. In our test, we noticed that when Auto retrieve MMS was disabled, videos took a few seconds longer to start playing because the app needed to initiate the download process.
Although this does not completely secure your phone, it lessens the chances that you’ll fall victim to the Stagefright MMS Hack in a big way.
We can’t offer you a 100-percent guarantee, but as long as you make sure Auto retrieve MMS is disabled and you never play a video via MMS from anyone you do not recognize, you should be okay until a patch is issued for your phone from the manufacturer and carrier.
How Google found out about the exploit
The exploit, which was discovered in April by Joshua Drake from Zimperium zLabs, comes from remote code execution bugs residing in the media playback tool in Android called Stagefright. Drake contacted Google and sent patches regarding the vulnerability on April 9, and Google immediately accepted them. Drake reported a second set of issues in May, bringing the total to seven vulnerabilities. Google confirmed that the patches were scheduled to be released, and now they have been sent out.
Google made the following statement: “We thank Joshua Drake for his contributions. The security of Android users is extremely important to us and so we responded quickly and patches have already been provided to partners that can be applied to any device.”
“Most Android devices, including all newer devices, have multiple technologies that are designed to make exploitation more difficult,” it continued. “Android devices also include an application sandbox designed to protect user data and other applications on the device.”
Unfortunately, there isn’t much the consumer can do while they wait for the patch beyond the steps we’ve listed in this article. What makes things more confusing is that the Messenger app that Drake refers to is a Google app and it’s the default SMS / MMS messaging app on Nexus devices. However, most Android phones don’t include Messenger in favor of one that is developed by the manufacturer of the phone. It’s unclear whether a hacker can gain access through something like Samsung’s own Messages app, which is found on all Galaxy phones.
Then there is the issue of the hackers needing to know your phone number, but what would stop someone from sending millions of random messages?
The good news is that hackers weren’t aware of the vulnerability, so it’s unlikely anyone is utilizing it at the moment. However, disclosures of the bugs have been released, which means that exploiters will have enough information to start writing code.
We’ll find out more about the Stagefright vulnerability when Drake demonstrates his findings at the Black Hat and Defcon security events August 6 in Las Vegas. We’ll keep you updated here.
—————
Previous updates:
Updated on 08-21-2015 by Robert Nazarian: Added news of a patch for the OnePlus 2.
Updated on 08-17-2015 by Kyle Wiggers: Added information about a new exploit discovered by security firm Exodus Intelligence.
Updated on 08-11-2015 by Kyle Wiggers: Reorganized and updated the list of phones that have received Stagefright patches.
Updated on 08-10-2015 by Robert Nazarian: Added which Motorola phones will get the Stagefright hack security patch
Updated on 08-07-2015 by Robert Nazarian: Added information regarding an app that will tell you if your phone is vulnerable to the Stagefright hack.
Updated on 08-07-2015 by Andy Boxall: Added a statement from ZTE on its plans to secure phones against Stagefright
Updated on 08-05-2015 by Malarie Gokey: Added list of devices with the security patch, including news of the update directly from Google.
Updated on 07-31-2015 by Robert Nazarian: Added information on how users can defend themselves from the Stagefright MMS attack while waiting for a patch update.